Hi
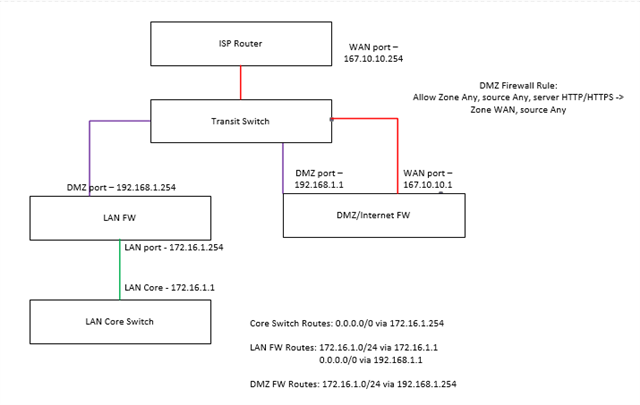
First of all a quick brief on our set up.
we have two DCs, both DCs have a HA pair of firewalls controlling our LAN traffic. We also have a HA pair of firewalls across both DCs for DMZ and Internet traffic.
Our LAN firewalls have a leg in the DMZ and all internal routing seems fine (all sites can route to the DMZ primary firewall and vice versa)
Our LAN firewalls are configure to route all DMZ and external traffic to our Internet/DMZ firewall and all LAN traffic via VPLS. Again, LAN access to DMZ servers is working fine.
The issue is breaking out to the internet. I have tried several types of rules (including even very briefly trying an allow any/any, along with various NAT rules) but I cannot get out to the internet.
Running a packet capture from the LAN FW I can see the traffic passing to the DMZ interface. On the DMZ FW I can see the packet in on the DMZ interface and out of the WAN interface. However the packet states it’s a violation with the reason as Firewall.
I have double checked routing, I’ve made strict and then very open rules to test, but I am running out of ideas!
Does anyone have any suggestions or pointers for troubleshooting? The information I’m getting doesnt seem to help me in anyway
thanks
This thread was automatically locked due to age.