Hi Guys
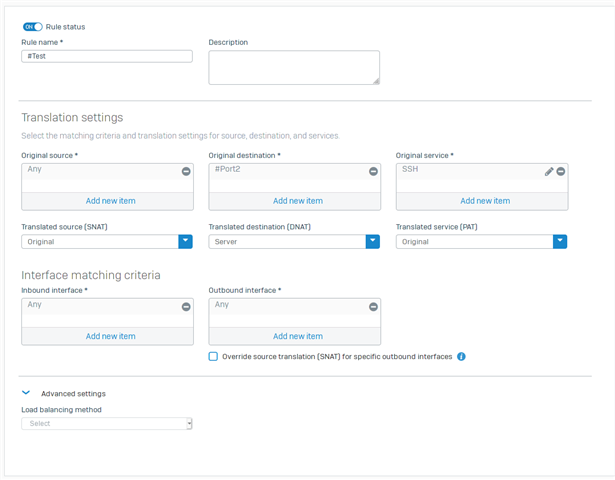
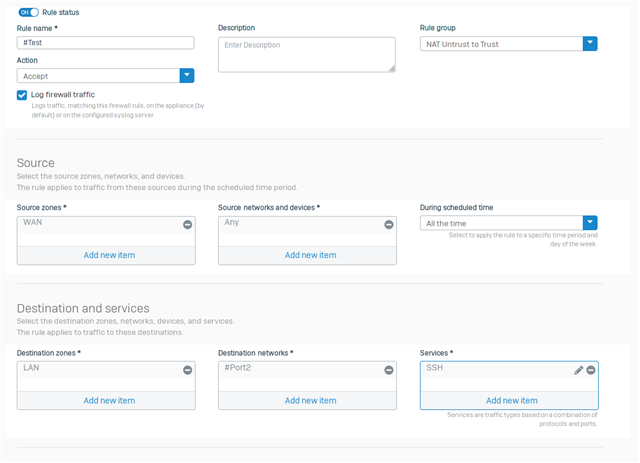
I have a program called SilverShield which is SFTP program behind UTM and realized that it has DNAT set up on UTM. I am trying to set up DNAT on XG which has more options and tried a few it does not work. By looking at below screenshot, is there a way of saying or showing me how i could mock this DNAT rule on XG?
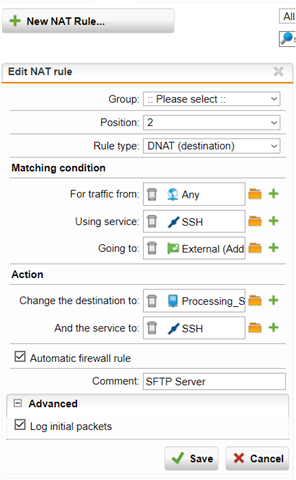
Change the destination to: It's the Server where i have the Silvershield sftp program installed. When I try I get winSCP saying that Access Denied. I've checked Azure all the SecurityGroups are allowing Port 22. I can SSH the XG no problem, but to this program I can not.. I think i need to set up DNAT in order to access to the server and the program?
Thanks in advance.
Regards
This thread was automatically locked due to age.