XG330 (SFOS 17.5.12 MR-12)
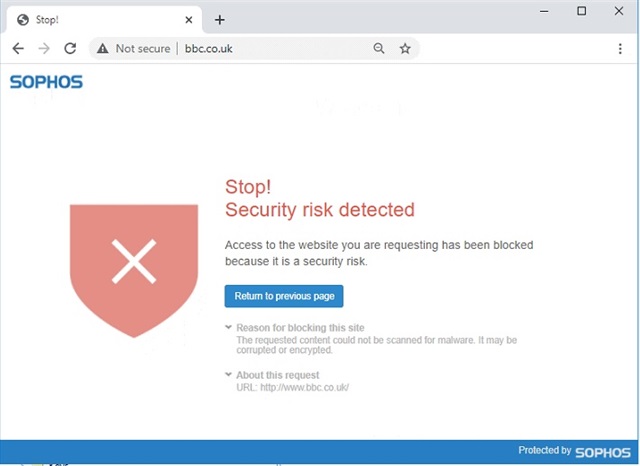
Since firewall reboot last night our XG is now blocking all HTTP sites and displaying the following page. We have not made any changes to any rules, and the HTTPS version of the site works fine.
More critically, there are no entries in the log viewer for these blocks to help diagnose which area of the XG is causing this block.
This thread was automatically locked due to age.