Hi all,
i have kind of a strange problem.
For information: I have worked with Securepoint Firewalls prior to Sophos and now and then with the UTM.
Now we have switched to the XG (450).
Background: The Sophos builds an IPSEC from the head office into the Azure infrastructure, offers LDAPS / AAD / RADIUS etc ... everything working fine so far.
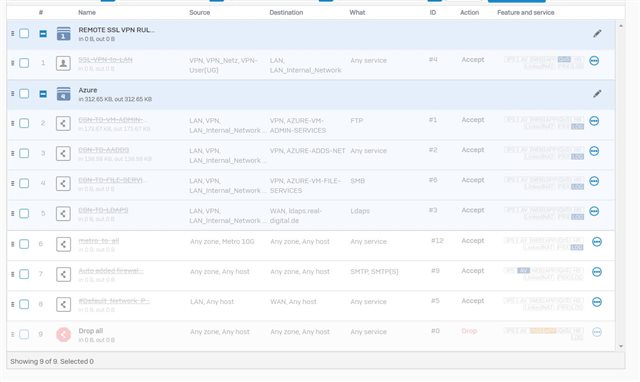
The SSL-VPN users (10.242.0.2) have an extra set of rules, where it is specified which machines on Azure side can be reached on which ports.
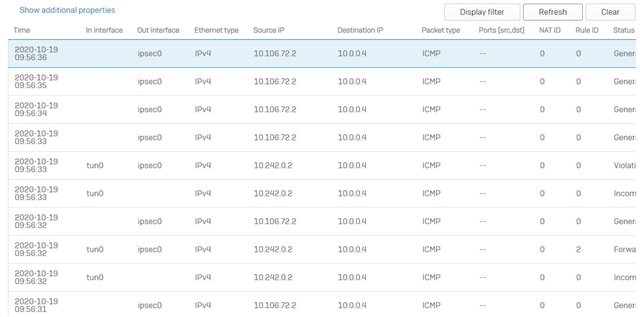
I am just amazed that e.g. Traffic from the console of the firewall itself goes through from the LAN interface (10.106.72.2) and this traffic with RULE ID 0 goes through without any existing outbound rule.
If I compare that with SSL-VPN traffic, nothing goes through until I activate the corresponding outbound rules. Here in the picture this is rule 2, which is recognized and takes effect.
I once read about it, (https://community.sophos.com/xg-firewall/sfos-eap/sfos-v18-early-access-program/f/feedback-and-issues/115743/traffic-is-allowed-out-lan-wan-when-no-lan-wan-fw-rules-exist-i-e-traffic-goes-out-via-rule-0)if there is outbound traffic despite the explicitly missing outbound rule, the XG is not properly licensed. But I see an active license until 2023 in the firewall itself and in the MySophos account.
Anyone have an idea?
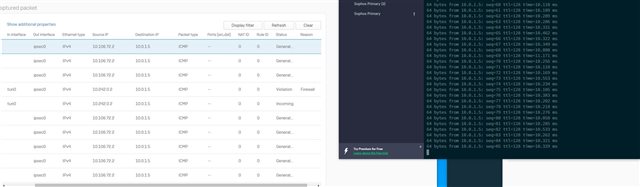
In this pic you see that traffic from SSL-VPN gets denied. Thats totally ok, as i deactivated the rule, but traffic from LAN-Interface goes into the IPSEC Tunnel without having a rule???
All existing rules on the XG
This thread was automatically locked due to age.


