Hello,
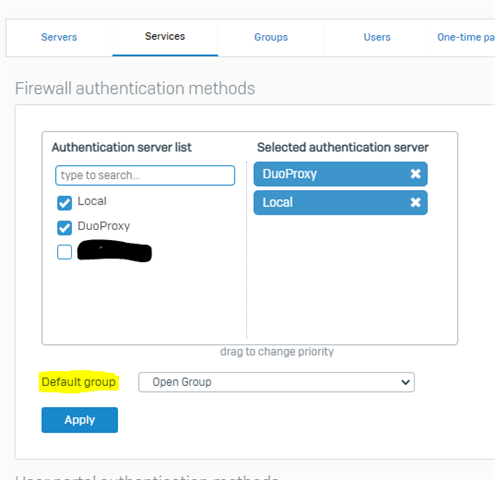
I have integrated Cisco Duo with Sophos XG (running firmware 18.01), but have issues with SSL VPN. My AD is my Primary authentication method, while Duo is my second factor authentication. When I test connection, all works well.
I have changed the SSL authentication method to use Duo first, when I try to VPN, I do receive a PUSH which I approve, but still fails (wrong username or something like that). I see it on Duo as successful, but still would not work.
Has anyone done this integration recently on firmware 18 now that we can set timeout values.
Thanks.
This thread was automatically locked due to age.