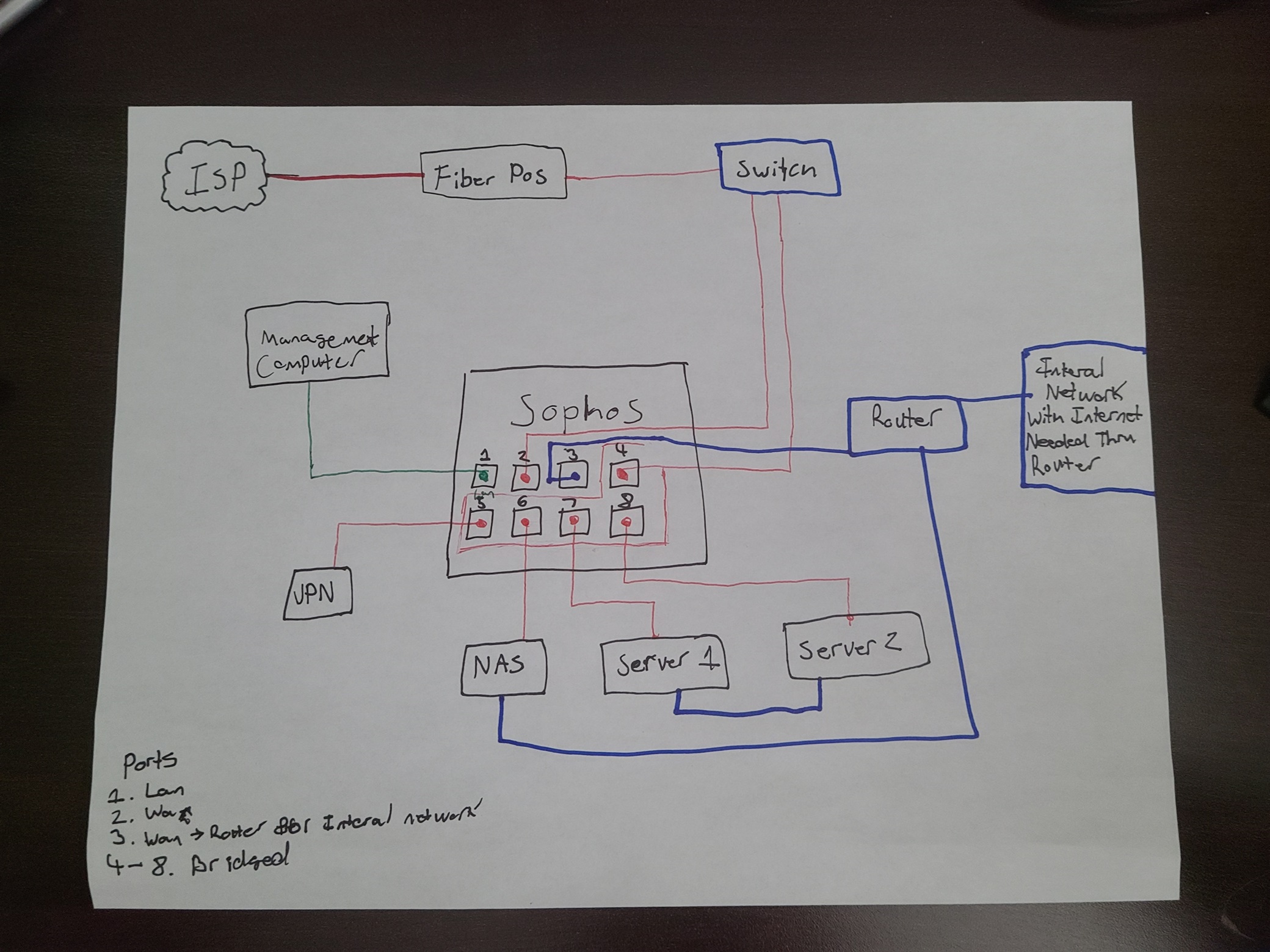
Here is the network topology that I am trying to achieve with the Sophos firewall. I'm not sure if this is the best way to do it. The big overview is to provide safe outside access to internal systems via a kind of mixed bridge system where each individual port is used for a specific device. The reason why I need to do this complicated bridged setup is because the ISP's Fiber POS DOESN'T ALLOW MULTIPLE IPS UNDER A SINGLE MAC ADDRESS. Why? Because they just don't. Talk about a pain in the butt.
Network static IP assignment comes from the ISP through the Fiber POS. The Fiber POS operates on the Data Link Layer (Layer 2 from OSI model) and assigns static IP addresses on the MAC sublayer. Explained more below a single ethernet cord will run from the Fiber POS to a switch.
The switch will have port 1 used for the Fiber POS. Switch port 2 will go into port 2 of the Sophos Firewall. Port 3 will go into port 4 of the Sophos Firewall.
To make sure that the Sophos Firewall has internet (for updates) and is able to be connected to with it's VPN the Wan Port (port 2) will be fed an ethernet connection from the switch. This will allow the Fiber POS to assign a static IP to the Sophos firewall [already done].
On port 1 of the Sophos Firewall there will be a connection for management of the Sophos Firewall on a connected Management Computer [already done]. This computer will have internet through the Wan Port (port 2) but can not talk to anything on the internal network with the exception of the Sophos Firewall.
On port 3 the Sophos firewall will run a DHCP server on this port and assign an IP to the router which will allow internet connectivity to the internal network.
On port 4 the Sophos Firewall will receive an ethernet cord from the switch. This will allow bridging on ports 4-8 of the Sophos Firewall where the Fiber POS is able to assign Static IP addresses being that it will be able to see the connected device's Mac Addresses.
On port 5 is a network VPN which is used for secure static connection into the NAS and outside networks. In all intents and purposes it acts as a server.
On port 6 is the network NAS. This has two ethernet ports where one is for the open network and one is for the internal network. There are many things running on this but it gets assigned a static IP for outside connections and a internal IP from the router for high-speed internal network access.
Port 7 and 8 will be used for two servers in a kind of fall over arrangement. These servers will be connected AFTER the firewall setup is done.
If you have any questions let me know. The basic idea is the isolation of three networks. One for public access used as a secure bridge, one for internal internet access, and one for firewall management access.
Ports 6-8 will require SSL offloading being that all of them have a webserver running a HTTPS connection. The VPN and the NAS also has IP assignment.
I'm not sure if this is the best method to get it done. Any guidance would be great. It's complicated and I completely believe there is a way to simply it. I don't want to use many switches because the installation area is quite small and with the addition of two servers it's going to be a tight fit.
Jordan Roy
This thread was automatically locked due to age.