Hello,
Here is my scenario:
Head Office network 192.168.200.0/22 and gateway 192.168.200.11 (XG)
Branch Office network 172.16.16.0/24 and gateway 172.16.16.16 (XG)
Both firewalls are running on 18.0.2
VPN IPSEC site-to-site established successfully.
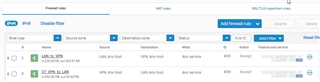
Both firewalls have the same set of rules, one for traffic from LAN to VPN any host and another for traffic from VPN to LAN any host.
From Branch Office XG I can ping the Head Office XG on its LAN IP
But from Head Office XG I cannot ping the Branch Office XG on its LAN IP
Analyzing on Log Viewer I can see that the Head Office XG identified the 172.16.16.0 remote network as part of the WAN zone and the traffic is ignoring the rule I created for VPN traffic.
I have already tried to change the route precedence in SSH but still no luck
This thread was automatically locked due to age.