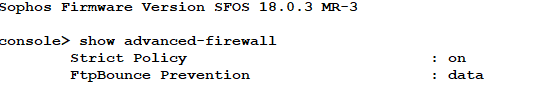
We utilize a poorly written piece of software from the Federal government that sends and receives files over FTP using a non standard port (port 26581). After we installed our new XG 550 the send and receive has stopped working entirely. We got it to work 1 time and we still aren't sure why it worked. This is a mission critical software for us and the Feds will not allow us to send it any other way besides this specifically written piece of software. We have an escalated ticket with Sophos and they are working as quickly as they can, but I wanted to see if anyone out in the world has experienced something similar with FTP?
The XG 550 is running version 18.0.1 where our last XG ran 17.5.14
We have tried firewall rules allowing all traffic to and from the box, and tried just about every trick we can think of to no avail. We can't go outside the firewall to bypass for a variety of reasons. Appears that the XG is sending reset packets on the return traffic for some oddball reason. Any assistance would be greatly appreciated.
This thread was automatically locked due to age.