Appliance XG 135
SFOS 18.0.1 MR-1
Hello everybody,
since deploying the xg firewall appliance we encountered an issue with one of our external servers. All services hosted on this server become randomly unavailable because of a timeout while doing the ssl handshake. The client sends the ClientHello command and the server does not respond with a ServerHello command. During the period of not responding (about 5-10 minutes) the server is reachable through other networks which don't get routed through the firewall i.e. other DSL connections, mobile, etc.
Currently only the firewall and nat rules are setuped, no policies whatsoever are applied.
I also did a tcpdump and it shows the same as a manual get request over curl. The clients sends ClientHello and the server does not respond.
The only things that get logged are invalid packets and packets that don't correspond to an active connection. As you can see in the attached screenshot. 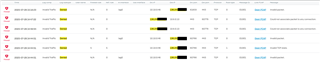
Do you have any idea what the issue could be?
This thread was automatically locked due to age.




