Hello,
Im planning the upgrade from SFOS v17 to v18, and Im testing my current configs. Currently Im facing a problem with IPSEC tunnels and SD-WAN (with load balance) and SNAT rules.
Based in documentations and videos about theses features:
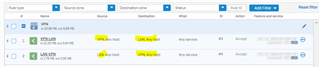
Im having problems with IPSEC traffic. All traffic from LAN ZONE to VPN ZONE is using the WAN Gateway insted usage ipsec tunnel/route.
Could someone tell me what is the best and correct way to usage SD-WAN/ SNAT / Load Balance withou impact in IPSEC ?
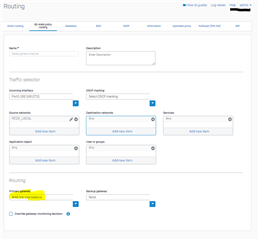
Im attaching my configs based in videos and dcoumentations
Best regards
Carlos
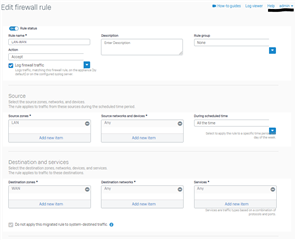
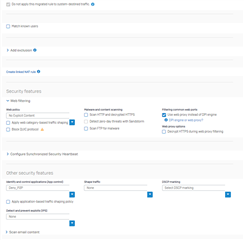
Firewall Rule
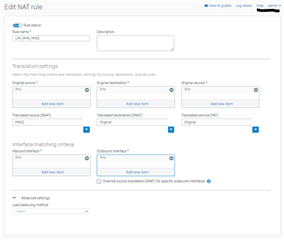
NAT RULE
This thread was automatically locked due to age.