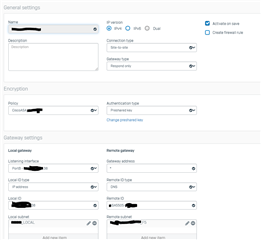
Hello,
Currently I have the following scenario
1 - Cisco ASA 5512 in Head Office with
Static WAN IP Address
LAN Interface
And 10 Branch office peers running Cisco ASA 5505, all B.O peers has a WAN Dynamic IP address
Currently this following scnenario is connected with IPSEC VPN, H.O peer as responder and B.O peers as initiators. This is working as expected currently.
We have planning replace the H.O device By SOPHOS XG, but we are facing problems with IPSEC.
When I try establish a VPN Ipsec from B.O Cisco 5505 (as initiator) to Sophos XG (Respond Only), the Tunnel does not UP, but If I try establish the VPN from Sophos XG (as Initiator) to B.O Cisco 5505 (as responder) with the same configs, except changing the initiator/responder functions the tunel goes UP. But I cannot keep the configs with this mode, due all B.O peers has dynamic WAN IP address.
Does someone has any tip to fix it ?
Im attaching the charon log file with the errors.
Regards
Carlos
2020-07-21 08:27:50 19[NET] <2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (172 bytes) 2020-07-21 08:27:50 19[ENC] <2> parsed ID_PROT request 0 [ SA V V V V ] 2020-07-21 08:27:50 19[IKE] <2> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID 2020-07-21 08:27:50 19[IKE] <2> received draft-ietf-ipsec-nat-t-ike-03 vendor ID 2020-07-21 08:27:50 19[IKE] <2> received NAT-T (RFC 3947) vendor ID 2020-07-21 08:27:50 19[IKE] <2> received FRAGMENTATION vendor ID 2020-07-21 08:27:50 19[IKE] <2> X.X.X.X is initiating a Main Mode IKE_SA 2020-07-21 08:27:50 19[ENC] <2> generating ID_PROT response 0 [ SA V V V V V ] 2020-07-21 08:27:50 19[NET] <2> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (184 bytes) 2020-07-21 08:27:50 16[NET] <2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (304 bytes) 2020-07-21 08:27:50 16[ENC] <2> parsed ID_PROT request 0 [ KE No V V V V NAT-D NAT-D ] 2020-07-21 08:27:50 16[IKE] <2> received Cisco Unity vendor ID 2020-07-21 08:27:50 16[IKE] <2> received XAuth vendor ID 2020-07-21 08:27:50 16[ENC] <2> received unknown vendor ID: 41:6f:45:e1:a8:0c:e1:e5:da:f5:7b:a6:1f:73:a2:54 2020-07-21 08:27:50 16[ENC] <2> received unknown vendor ID: 1f:07:f7:0e:aa:65:14:d3:b0:fa:96:54:2a:50:01:00 2020-07-21 08:27:50 16[ENC] <2> generating ID_PROT response 0 [ KE No NAT-D NAT-D ] 2020-07-21 08:27:50 16[NET] <2> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (244 bytes) 2020-07-21 08:27:50 08[NET] <2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:27:50 08[ENC] <2> parsed ID_PROT request 0 [ ID HASH V ] 2020-07-21 08:27:50 08[IKE] <2> received DPD vendor ID 2020-07-21 08:27:50 08[CFG] <2> looking for pre-shared key peer configs matching Y.Y.Y.Y...X.X.X.X[X.X.X.X] 2020-07-21 08:27:50 08[CFG] <2> selected peer config "Connection-Ipsec1" 2020-07-21 08:27:50 08[IKE] <Connection-Ipsec1|2> IKE_SA Connection-Ipsec1[2] established between Y.Y.Y.Y[Y.Y.Y.Y]...X.X.X.X[X.X.X.X] 2020-07-21 08:27:50 08[IKE] <Connection-Ipsec1|2> scheduling rekeying in 85876s 2020-07-21 08:27:50 08[IKE] <Connection-Ipsec1|2> maximum IKE_SA lifetime 86236s 2020-07-21 08:27:50 08[ENC] <Connection-Ipsec1|2> generating ID_PROT response 0 [ ID HASH ] 2020-07-21 08:27:50 08[NET] <Connection-Ipsec1|2> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:27:50 10[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:27:50 10[ENC] <Connection-Ipsec1|2> parsed QUICK_MODE request 4189536779 [ HASH SA No ID ID N(INITIAL_CONTACT) ] 2020-07-21 08:27:50 10[IKE] <Connection-Ipsec1|2> ### process_request invoking quick_mode_create 2020-07-21 08:27:50 10[IKE] <Connection-Ipsec1|2> ### quick_mode_create: 0x7f239c001080 config (nil) 2020-07-21 08:27:50 10[IKE] <Connection-Ipsec1|2> ### process_r: 0x7f239c001080 QM_INIT 2020-07-21 08:27:50 10[IKE] <Connection-Ipsec1|2> trying other candidates from phase 1 2020-07-21 08:27:50 10[IKE] <Connection-Ipsec1|2> no matching CHILD_SA config found 2020-07-21 08:27:50 10[IKE] <Connection-Ipsec1|2> ### destroy: 0x7f239c001080 2020-07-21 08:27:50 10[ENC] <Connection-Ipsec1|2> generating INFORMATIONAL_V1 request 718700361 [ HASH N(INVAL_ID) ] 2020-07-21 08:27:50 10[NET] <Connection-Ipsec1|2> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:27:58 18[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:27:58 18[IKE] <Connection-Ipsec1|2> received retransmit of request with ID 4189536779, but no response to retransmit 2020-07-21 08:28:06 07[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:28:06 07[IKE] <Connection-Ipsec1|2> received retransmit of request with ID 4189536779, but no response to retransmit 2020-07-21 08:28:06 26[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:28:06 26[ENC] <Connection-Ipsec1|2> parsed INFORMATIONAL_V1 request 888691207 [ HASH N(DPD) ] 2020-07-21 08:28:06 26[ENC] <Connection-Ipsec1|2> generating INFORMATIONAL_V1 request 2750751797 [ HASH N(DPD_ACK) ] 2020-07-21 08:28:06 26[NET] <Connection-Ipsec1|2> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (92 bytes) 2020-07-21 08:28:14 27[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:28:14 27[ENC] <Connection-Ipsec1|2> invalid HASH_V1 payload length, decryption failed? 2020-07-21 08:28:14 27[ENC] <Connection-Ipsec1|2> could not decrypt payloads 2020-07-21 08:28:14 27[IKE] <Connection-Ipsec1|2> message parsing failed 2020-07-21 08:28:14 27[ENC] <Connection-Ipsec1|2> generating INFORMATIONAL_V1 request 197386102 [ HASH N(PLD_MAL) ] 2020-07-21 08:28:14 27[NET] <Connection-Ipsec1|2> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:28:14 27[IKE] <Connection-Ipsec1|2> QUICK_MODE request with message ID 4189536779 processing failed 2020-07-21 08:28:14 27[DMN] <Connection-Ipsec1|2> [GARNER-LOGGING] (child_alert) ALERT: parsing IKE message from X.X.X.X[500] failed 2020-07-21 08:28:16 25[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:28:16 25[ENC] <Connection-Ipsec1|2> parsed INFORMATIONAL_V1 request 253168492 [ HASH N(DPD) ] 2020-07-21 08:28:16 25[ENC] <Connection-Ipsec1|2> generating INFORMATIONAL_V1 request 427611669 [ HASH N(DPD_ACK) ] 2020-07-21 08:28:16 25[NET] <Connection-Ipsec1|2> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (92 bytes) 2020-07-21 08:28:22 12[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (76 bytes) 2020-07-21 08:28:22 12[ENC] <Connection-Ipsec1|2> parsed INFORMATIONAL_V1 request 3114948339 [ HASH D ] 2020-07-21 08:28:22 12[IKE] <Connection-Ipsec1|2> received DELETE for ESP CHILD_SA with SPI 5daf6325 2020-07-21 08:28:22 12[IKE] <Connection-Ipsec1|2> CHILD_SA not found, ignored 2020-07-21 08:28:22 15[NET] <Connection-Ipsec1|2> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:28:22 15[ENC] <Connection-Ipsec1|2> parsed INFORMATIONAL_V1 request 880126733 [ HASH D ] 2020-07-21 08:28:22 15[IKE] <Connection-Ipsec1|2> received DELETE for IKE_SA Connection-Ipsec1[2] 2020-07-21 08:28:22 15[IKE] <Connection-Ipsec1|2> deleting IKE_SA Connection-Ipsec1[2] between Y.Y.Y.Y[Y.Y.Y.Y]...X.X.X.X[X.X.X.X] 2020-07-21 08:28:22 30[NET] <3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (172 bytes) 2020-07-21 08:28:22 30[ENC] <3> parsed ID_PROT request 0 [ SA V V V V ] 2020-07-21 08:28:22 30[IKE] <3> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID 2020-07-21 08:28:22 30[IKE] <3> received draft-ietf-ipsec-nat-t-ike-03 vendor ID 2020-07-21 08:28:22 30[IKE] <3> received NAT-T (RFC 3947) vendor ID 2020-07-21 08:28:22 30[IKE] <3> received FRAGMENTATION vendor ID 2020-07-21 08:28:22 30[IKE] <3> X.X.X.X is initiating a Main Mode IKE_SA 2020-07-21 08:28:22 30[ENC] <3> generating ID_PROT response 0 [ SA V V V V V ] 2020-07-21 08:28:22 30[NET] <3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (184 bytes) 2020-07-21 08:28:22 17[NET] <3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (304 bytes) 2020-07-21 08:28:22 17[ENC] <3> parsed ID_PROT request 0 [ KE No V V V V NAT-D NAT-D ] 2020-07-21 08:28:22 17[IKE] <3> received Cisco Unity vendor ID 2020-07-21 08:28:22 17[IKE] <3> received XAuth vendor ID 2020-07-21 08:28:22 17[ENC] <3> received unknown vendor ID: b1:b5:6d:4f:e6:64:f3:5f:14:d3:58:75:86:e2:61:43 2020-07-21 08:28:22 17[ENC] <3> received unknown vendor ID: 1f:07:f7:0e:aa:65:14:d3:b0:fa:96:54:2a:50:01:00 2020-07-21 08:28:22 17[ENC] <3> generating ID_PROT response 0 [ KE No NAT-D NAT-D ] 2020-07-21 08:28:22 17[NET] <3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (244 bytes) 2020-07-21 08:28:22 24[NET] <3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:28:22 24[ENC] <3> parsed ID_PROT request 0 [ ID HASH V ] 2020-07-21 08:28:22 24[IKE] <3> received DPD vendor ID 2020-07-21 08:28:22 24[CFG] <3> looking for pre-shared key peer configs matching Y.Y.Y.Y...X.X.X.X[X.X.X.X] 2020-07-21 08:28:22 24[CFG] <3> selected peer config "Connection-Ipsec1" 2020-07-21 08:28:22 24[IKE] <Connection-Ipsec1|3> IKE_SA Connection-Ipsec1[3] established between Y.Y.Y.Y[Y.Y.Y.Y]...X.X.X.X[X.X.X.X] 2020-07-21 08:28:22 24[IKE] <Connection-Ipsec1|3> scheduling rekeying in 86015s 2020-07-21 08:28:22 24[IKE] <Connection-Ipsec1|3> maximum IKE_SA lifetime 86375s 2020-07-21 08:28:22 24[ENC] <Connection-Ipsec1|3> generating ID_PROT response 0 [ ID HASH ] 2020-07-21 08:28:22 24[NET] <Connection-Ipsec1|3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:28:22 18[NET] <Connection-Ipsec1|3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:28:22 18[ENC] <Connection-Ipsec1|3> parsed QUICK_MODE request 3952467841 [ HASH SA No ID ID N(INITIAL_CONTACT) ] 2020-07-21 08:28:22 18[IKE] <Connection-Ipsec1|3> ### process_request invoking quick_mode_create 2020-07-21 08:28:22 18[IKE] <Connection-Ipsec1|3> ### quick_mode_create: 0x7f2388000b90 config (nil) 2020-07-21 08:28:22 18[IKE] <Connection-Ipsec1|3> ### process_r: 0x7f2388000b90 QM_INIT 2020-07-21 08:28:22 18[IKE] <Connection-Ipsec1|3> trying other candidates from phase 1 2020-07-21 08:28:22 18[IKE] <Connection-Ipsec1|3> no matching CHILD_SA config found 2020-07-21 08:28:22 18[IKE] <Connection-Ipsec1|3> ### destroy: 0x7f2388000b90 2020-07-21 08:28:22 18[ENC] <Connection-Ipsec1|3> generating INFORMATIONAL_V1 request 1507847503 [ HASH N(INVAL_ID) ] 2020-07-21 08:28:22 18[NET] <Connection-Ipsec1|3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:28:30 26[NET] <Connection-Ipsec1|3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:28:30 26[IKE] <Connection-Ipsec1|3> received retransmit of request with ID 3952467841, but no response to retransmit 2020-07-21 08:28:36 25[NET] <Connection-Ipsec1|3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:28:36 25[ENC] <Connection-Ipsec1|3> parsed INFORMATIONAL_V1 request 199647637 [ HASH N(DPD) ] 2020-07-21 08:28:36 25[ENC] <Connection-Ipsec1|3> generating INFORMATIONAL_V1 request 3461264942 [ HASH N(DPD_ACK) ] 2020-07-21 08:28:36 25[NET] <Connection-Ipsec1|3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (92 bytes) 2020-07-21 08:28:38 11[NET] <Connection-Ipsec1|3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:28:38 11[ENC] <Connection-Ipsec1|3> invalid HASH_V1 payload length, decryption failed? 2020-07-21 08:28:38 11[ENC] <Connection-Ipsec1|3> could not decrypt payloads 2020-07-21 08:28:38 11[IKE] <Connection-Ipsec1|3> message parsing failed 2020-07-21 08:28:38 11[ENC] <Connection-Ipsec1|3> generating INFORMATIONAL_V1 request 2416882772 [ HASH N(PLD_MAL) ] 2020-07-21 08:28:38 11[NET] <Connection-Ipsec1|3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:28:38 11[IKE] <Connection-Ipsec1|3> QUICK_MODE request with message ID 3952467841 processing failed 2020-07-21 08:28:38 11[DMN] <Connection-Ipsec1|3> [GARNER-LOGGING] (child_alert) ALERT: parsing IKE message from X.X.X.X[500] failed 2020-07-21 08:28:46 18[NET] <Connection-Ipsec1|3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:28:46 18[ENC] <Connection-Ipsec1|3> parsed INFORMATIONAL_V1 request 945449334 [ HASH N(DPD) ] 2020-07-21 08:28:46 18[ENC] <Connection-Ipsec1|3> generating INFORMATIONAL_V1 request 2291819154 [ HASH N(DPD_ACK) ] 2020-07-21 08:28:46 18[NET] <Connection-Ipsec1|3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (92 bytes) 2020-07-21 08:28:46 31[NET] <Connection-Ipsec1|3> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:28:46 31[ENC] <Connection-Ipsec1|3> invalid HASH_V1 payload length, decryption failed? 2020-07-21 08:28:46 31[ENC] <Connection-Ipsec1|3> could not decrypt payloads 2020-07-21 08:28:46 31[IKE] <Connection-Ipsec1|3> message parsing failed 2020-07-21 08:28:46 31[ENC] <Connection-Ipsec1|3> generating INFORMATIONAL_V1 request 3251920000 [ HASH N(PLD_MAL) ] 2020-07-21 08:28:46 31[NET] <Connection-Ipsec1|3> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:28:46 31[IKE] <Connection-Ipsec1|3> QUICK_MODE request with message ID 3952467841 processing failed 2020-07-21 08:28:46 31[DMN] <Connection-Ipsec1|3> [GARNER-LOGGING] (child_alert) ALERT: parsing IKE message from X.X.X.X[500] failed 2020-07-21 08:38:54 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:38:54 03[NET] waiting for data on sockets 2020-07-21 08:38:54 13[NET] <32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (172 bytes) 2020-07-21 08:38:54 13[ENC] <32> parsed ID_PROT request 0 [ SA V V V V ] 2020-07-21 08:38:54 13[CFG] <32> looking for an ike config for Y.Y.Y.Y...X.X.X.X 2020-07-21 08:38:54 13[CFG] <32> candidate: Y.Y.Y.Y...%any, prio 1052 2020-07-21 08:38:54 13[CFG] <32> found matching ike config: Y.Y.Y.Y...%any with prio 1052 2020-07-21 08:38:54 13[IKE] <32> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID 2020-07-21 08:38:54 13[IKE] <32> received draft-ietf-ipsec-nat-t-ike-03 vendor ID 2020-07-21 08:38:54 13[IKE] <32> received NAT-T (RFC 3947) vendor ID 2020-07-21 08:38:54 13[IKE] <32> received FRAGMENTATION vendor ID 2020-07-21 08:38:54 13[IKE] <32> X.X.X.X is initiating a Main Mode IKE_SA 2020-07-21 08:38:54 13[IKE] <32> IKE_SA (unnamed)[32] state change: CREATED => CONNECTING 2020-07-21 08:38:54 13[CFG] <32> selecting proposal: 2020-07-21 08:38:54 13[CFG] <32> no acceptable DIFFIE_HELLMAN_GROUP found 2020-07-21 08:38:54 13[CFG] <32> selecting proposal: 2020-07-21 08:38:54 13[CFG] <32> proposal matches 2020-07-21 08:38:54 13[CFG] <32> received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 2020-07-21 08:38:54 13[CFG] <32> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_768, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048 2020-07-21 08:38:54 13[CFG] <32> selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 2020-07-21 08:38:54 13[IKE] <32> sending XAuth vendor ID 2020-07-21 08:38:54 13[IKE] <32> sending DPD vendor ID 2020-07-21 08:38:54 13[IKE] <32> sending Cisco Unity vendor ID 2020-07-21 08:38:54 13[IKE] <32> sending FRAGMENTATION vendor ID 2020-07-21 08:38:54 13[IKE] <32> sending NAT-T (RFC 3947) vendor ID 2020-07-21 08:38:54 13[ENC] <32> generating ID_PROT response 0 [ SA V V V V V ] 2020-07-21 08:38:54 13[NET] <32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (184 bytes) 2020-07-21 08:38:54 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:38:54 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:38:54 03[NET] waiting for data on sockets 2020-07-21 08:38:54 32[NET] <32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (304 bytes) 2020-07-21 08:38:54 32[ENC] <32> parsed ID_PROT request 0 [ KE No V V V V NAT-D NAT-D ] 2020-07-21 08:38:54 32[IKE] <32> received Cisco Unity vendor ID 2020-07-21 08:38:54 32[IKE] <32> received XAuth vendor ID 2020-07-21 08:38:54 32[ENC] <32> received unknown vendor ID: bc:62:5a:d9:d3:87:f0:4a:df:2b:32:4c:5b:b9:de:90 2020-07-21 08:38:54 32[ENC] <32> received unknown vendor ID: 1f:07:f7:0e:aa:65:14:d3:b0:fa:96:54:2a:50:01:00 2020-07-21 08:38:54 32[CFG] <32> candidate "Connection-Ipsec1", match: 1/1/1052 (me/other/ike) 2020-07-21 08:38:54 32[ENC] <32> generating ID_PROT response 0 [ KE No NAT-D NAT-D ] 2020-07-21 08:38:54 32[NET] <32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (244 bytes) 2020-07-21 08:38:54 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:38:54 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:38:54 03[NET] waiting for data on sockets 2020-07-21 08:38:54 17[NET] <32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:38:54 17[ENC] <32> parsed ID_PROT request 0 [ ID HASH V ] 2020-07-21 08:38:54 17[IKE] <32> received DPD vendor ID 2020-07-21 08:38:54 17[CFG] <32> looking for pre-shared key peer configs matching Y.Y.Y.Y...X.X.X.X[X.X.X.X] 2020-07-21 08:38:54 17[CFG] <32> candidate "Connection-Ipsec1", match: 1/1/1052 (me/other/ike) 2020-07-21 08:38:54 17[CFG] <32> selected peer config "Connection-Ipsec1" 2020-07-21 08:38:54 17[IKE] <Connection-Ipsec1|32> IKE_SA Connection-Ipsec1[32] established between Y.Y.Y.Y[Y.Y.Y.Y]...X.X.X.X[X.X.X.X] 2020-07-21 08:38:54 17[IKE] <Connection-Ipsec1|32> IKE_SA Connection-Ipsec1[32] state change: CONNECTING => ESTABLISHED 2020-07-21 08:38:54 17[IKE] <Connection-Ipsec1|32> scheduling rekeying in 85913s 2020-07-21 08:38:54 17[IKE] <Connection-Ipsec1|32> maximum IKE_SA lifetime 86273s 2020-07-21 08:38:54 17[ENC] <Connection-Ipsec1|32> generating ID_PROT response 0 [ ID HASH ] 2020-07-21 08:38:54 17[NET] <Connection-Ipsec1|32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:38:54 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:38:54 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:38:54 03[NET] waiting for data on sockets 2020-07-21 08:38:54 25[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:38:54 25[ENC] <Connection-Ipsec1|32> parsed QUICK_MODE request 1018731067 [ HASH SA No ID ID N(INITIAL_CONTACT) ] 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> ### process_request invoking quick_mode_create 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> ### quick_mode_create: 0x7f237c001f10 config (nil) 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> ### process_r: 0x7f237c001f10 QM_INIT 2020-07-21 08:38:54 25[CFG] <Connection-Ipsec1|32> looking for a child config for Y.Y.Y.Y/32 === X.X.X.X/32 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> trying other candidates from phase 1 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> no matching CHILD_SA config found 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> queueing INFORMATIONAL task, already 0 tasks queued 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> flush_queue(IKE_NATD) 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> ### destroy: 0x7f237c001f10 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> activating INFORMATIONAL task 2020-07-21 08:38:54 25[ENC] <Connection-Ipsec1|32> generating INFORMATIONAL_V1 request 4092525943 [ HASH N(INVAL_ID) ] 2020-07-21 08:38:54 25[NET] <Connection-Ipsec1|32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:38:54 25[IKE] <Connection-Ipsec1|32> nothing to initiate 2020-07-21 08:38:54 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:02 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:02 03[NET] waiting for data on sockets 2020-07-21 08:39:02 07[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:39:02 07[IKE] <Connection-Ipsec1|32> received retransmit of request with ID 1018731067, but no response to retransmit 2020-07-21 08:39:06 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:06 03[NET] waiting for data on sockets 2020-07-21 08:39:06 20[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:39:06 20[ENC] <Connection-Ipsec1|32> parsed INFORMATIONAL_V1 request 1588167248 [ HASH N(DPD) ] 2020-07-21 08:39:06 20[IKE] <Connection-Ipsec1|32> queueing ISAKMP_R_U_THERE_ACK task, already 0 tasks queued 2020-07-21 08:39:06 20[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:39:06 20[IKE] <Connection-Ipsec1|32> activating ISAKMP_R_U_THERE_ACK task 2020-07-21 08:39:06 20[ENC] <Connection-Ipsec1|32> generating INFORMATIONAL_V1 request 629011947 [ HASH N(DPD_ACK) ] 2020-07-21 08:39:06 20[NET] <Connection-Ipsec1|32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (92 bytes) 2020-07-21 08:39:06 20[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:39:06 20[IKE] <Connection-Ipsec1|32> nothing to initiate 2020-07-21 08:39:06 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:10 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:10 03[NET] waiting for data on sockets 2020-07-21 08:39:10 21[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:39:10 21[ENC] <Connection-Ipsec1|32> invalid HASH_V1 payload length, decryption failed? 2020-07-21 08:39:10 21[ENC] <Connection-Ipsec1|32> could not decrypt payloads 2020-07-21 08:39:10 21[IKE] <Connection-Ipsec1|32> message parsing failed 2020-07-21 08:39:10 21[ENC] <Connection-Ipsec1|32> generating INFORMATIONAL_V1 request 2732225861 [ HASH N(PLD_MAL) ] 2020-07-21 08:39:10 21[NET] <Connection-Ipsec1|32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:39:10 21[IKE] <Connection-Ipsec1|32> QUICK_MODE request with message ID 1018731067 processing failed 2020-07-21 08:39:10 21[DMN] <Connection-Ipsec1|32> [GARNER-LOGGING] (child_alert) ALERT: parsing IKE message from X.X.X.X[500] failed 2020-07-21 08:39:10 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:16 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:16 03[NET] waiting for data on sockets 2020-07-21 08:39:16 27[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:39:16 27[ENC] <Connection-Ipsec1|32> parsed INFORMATIONAL_V1 request 1176668260 [ HASH N(DPD) ] 2020-07-21 08:39:16 27[IKE] <Connection-Ipsec1|32> queueing ISAKMP_R_U_THERE_ACK task, already 0 tasks queued 2020-07-21 08:39:16 27[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:39:16 27[IKE] <Connection-Ipsec1|32> activating ISAKMP_R_U_THERE_ACK task 2020-07-21 08:39:16 27[ENC] <Connection-Ipsec1|32> generating INFORMATIONAL_V1 request 1918156880 [ HASH N(DPD_ACK) ] 2020-07-21 08:39:16 27[NET] <Connection-Ipsec1|32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (92 bytes) 2020-07-21 08:39:16 27[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:39:16 27[IKE] <Connection-Ipsec1|32> nothing to initiate 2020-07-21 08:39:16 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:18 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:18 03[NET] waiting for data on sockets 2020-07-21 08:39:18 11[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:39:18 11[ENC] <Connection-Ipsec1|32> invalid HASH_V1 payload length, decryption failed? 2020-07-21 08:39:18 11[ENC] <Connection-Ipsec1|32> could not decrypt payloads 2020-07-21 08:39:18 11[IKE] <Connection-Ipsec1|32> message parsing failed 2020-07-21 08:39:18 11[ENC] <Connection-Ipsec1|32> generating INFORMATIONAL_V1 request 2342623382 [ HASH N(PLD_MAL) ] 2020-07-21 08:39:18 11[NET] <Connection-Ipsec1|32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:39:18 11[IKE] <Connection-Ipsec1|32> QUICK_MODE request with message ID 1018731067 processing failed 2020-07-21 08:39:18 11[DMN] <Connection-Ipsec1|32> [GARNER-LOGGING] (child_alert) ALERT: parsing IKE message from X.X.X.X[500] failed 2020-07-21 08:39:18 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:26 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:26 03[NET] waiting for data on sockets 2020-07-21 08:39:26 25[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:39:26 25[ENC] <Connection-Ipsec1|32> parsed INFORMATIONAL_V1 request 3450490453 [ HASH N(DPD) ] 2020-07-21 08:39:26 25[IKE] <Connection-Ipsec1|32> queueing ISAKMP_R_U_THERE_ACK task, already 0 tasks queued 2020-07-21 08:39:26 25[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:39:26 25[IKE] <Connection-Ipsec1|32> activating ISAKMP_R_U_THERE_ACK task 2020-07-21 08:39:26 25[ENC] <Connection-Ipsec1|32> generating INFORMATIONAL_V1 request 471190235 [ HASH N(DPD_ACK) ] 2020-07-21 08:39:26 25[NET] <Connection-Ipsec1|32> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (92 bytes) 2020-07-21 08:39:26 25[IKE] <Connection-Ipsec1|32> activating new tasks 2020-07-21 08:39:26 25[IKE] <Connection-Ipsec1|32> nothing to initiate 2020-07-21 08:39:26 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:26 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:26 03[NET] waiting for data on sockets 2020-07-21 08:39:26 15[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (76 bytes) 2020-07-21 08:39:26 15[ENC] <Connection-Ipsec1|32> parsed INFORMATIONAL_V1 request 32248273 [ HASH D ] 2020-07-21 08:39:26 15[IKE] <Connection-Ipsec1|32> received DELETE for ESP CHILD_SA with SPI 32e8bbb2 2020-07-21 08:39:26 15[IKE] <Connection-Ipsec1|32> CHILD_SA not found, ignored 2020-07-21 08:39:26 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:26 03[NET] waiting for data on sockets 2020-07-21 08:39:26 05[NET] <Connection-Ipsec1|32> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:39:26 05[ENC] <Connection-Ipsec1|32> parsed INFORMATIONAL_V1 request 3597239554 [ HASH D ] 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> received DELETE for IKE_SA Connection-Ipsec1[32] 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> deleting IKE_SA Connection-Ipsec1[32] between Y.Y.Y.Y[Y.Y.Y.Y]...X.X.X.X[X.X.X.X] 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> IKE_SA Connection-Ipsec1[32] state change: ESTABLISHED => DELETING 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> IKE_SA Connection-Ipsec1[32] state change: DELETING => DELETING 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> flush_queue(IKE_MOBIKE) 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> flush_queue(IKE_NATD) 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> flush_queue(IKE_INIT) 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> IKE_SA Connection-Ipsec1[32] state change: DELETING => DESTROYING 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> flush_queue(IKE_MOBIKE) 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> flush_queue(IKE_NATD) 2020-07-21 08:39:26 05[IKE] <Connection-Ipsec1|32> flush_queue(IKE_INIT) 2020-07-21 08:39:26 05[IKE] flush_queue(IKE_MOBIKE) 2020-07-21 08:39:26 05[IKE] flush_queue(IKE_NATD) 2020-07-21 08:39:26 05[IKE] flush_queue(IKE_INIT) 2020-07-21 08:39:26 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:26 03[NET] waiting for data on sockets 2020-07-21 08:39:26 12[NET] <33> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (172 bytes) 2020-07-21 08:39:26 12[ENC] <33> parsed ID_PROT request 0 [ SA V V V V ] 2020-07-21 08:39:26 12[CFG] <33> looking for an ike config for Y.Y.Y.Y...X.X.X.X 2020-07-21 08:39:26 12[CFG] <33> candidate: Y.Y.Y.Y...%any, prio 1052 2020-07-21 08:39:26 12[CFG] <33> found matching ike config: Y.Y.Y.Y...%any with prio 1052 2020-07-21 08:39:26 12[IKE] <33> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID 2020-07-21 08:39:26 12[IKE] <33> received draft-ietf-ipsec-nat-t-ike-03 vendor ID 2020-07-21 08:39:26 12[IKE] <33> received NAT-T (RFC 3947) vendor ID 2020-07-21 08:39:26 12[IKE] <33> received FRAGMENTATION vendor ID 2020-07-21 08:39:26 12[IKE] <33> X.X.X.X is initiating a Main Mode IKE_SA 2020-07-21 08:39:26 12[IKE] <33> IKE_SA (unnamed)[33] state change: CREATED => CONNECTING 2020-07-21 08:39:26 12[CFG] <33> selecting proposal: 2020-07-21 08:39:26 12[CFG] <33> no acceptable DIFFIE_HELLMAN_GROUP found 2020-07-21 08:39:26 12[CFG] <33> selecting proposal: 2020-07-21 08:39:26 12[CFG] <33> proposal matches 2020-07-21 08:39:26 12[CFG] <33> received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 2020-07-21 08:39:26 12[CFG] <33> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_768, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048 2020-07-21 08:39:26 12[CFG] <33> selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 2020-07-21 08:39:26 12[IKE] <33> sending XAuth vendor ID 2020-07-21 08:39:26 12[IKE] <33> sending DPD vendor ID 2020-07-21 08:39:26 12[IKE] <33> sending Cisco Unity vendor ID 2020-07-21 08:39:26 12[IKE] <33> sending FRAGMENTATION vendor ID 2020-07-21 08:39:26 12[IKE] <33> sending NAT-T (RFC 3947) vendor ID 2020-07-21 08:39:26 12[ENC] <33> generating ID_PROT response 0 [ SA V V V V V ] 2020-07-21 08:39:26 12[NET] <33> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (184 bytes) 2020-07-21 08:39:26 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:26 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:26 03[NET] waiting for data on sockets 2020-07-21 08:39:26 14[NET] <33> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (304 bytes) 2020-07-21 08:39:26 14[ENC] <33> parsed ID_PROT request 0 [ KE No V V V V NAT-D NAT-D ] 2020-07-21 08:39:26 14[IKE] <33> received Cisco Unity vendor ID 2020-07-21 08:39:26 14[IKE] <33> received XAuth vendor ID 2020-07-21 08:39:26 14[ENC] <33> received unknown vendor ID: b6:d2:67:7a:c7:2e:b1:15:f4:0b:3e:28:58:33:ac:81 2020-07-21 08:39:26 14[ENC] <33> received unknown vendor ID: 1f:07:f7:0e:aa:65:14:d3:b0:fa:96:54:2a:50:01:00 2020-07-21 08:39:26 14[CFG] <33> candidate "Connection-Ipsec1", match: 1/1/1052 (me/other/ike) 2020-07-21 08:39:26 14[ENC] <33> generating ID_PROT response 0 [ KE No NAT-D NAT-D ] 2020-07-21 08:39:26 14[NET] <33> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (244 bytes) 2020-07-21 08:39:26 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:26 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:26 03[NET] waiting for data on sockets 2020-07-21 08:39:26 28[NET] <33> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (92 bytes) 2020-07-21 08:39:26 28[ENC] <33> parsed ID_PROT request 0 [ ID HASH V ] 2020-07-21 08:39:26 28[IKE] <33> received DPD vendor ID 2020-07-21 08:39:26 28[CFG] <33> looking for pre-shared key peer configs matching Y.Y.Y.Y...X.X.X.X[X.X.X.X] 2020-07-21 08:39:26 28[CFG] <33> candidate "Connection-Ipsec1", match: 1/1/1052 (me/other/ike) 2020-07-21 08:39:26 28[CFG] <33> selected peer config "Connection-Ipsec1" 2020-07-21 08:39:26 28[IKE] <Connection-Ipsec1|33> IKE_SA Connection-Ipsec1[33] established between Y.Y.Y.Y[Y.Y.Y.Y]...X.X.X.X[X.X.X.X] 2020-07-21 08:39:26 28[IKE] <Connection-Ipsec1|33> IKE_SA Connection-Ipsec1[33] state change: CONNECTING => ESTABLISHED 2020-07-21 08:39:26 28[IKE] <Connection-Ipsec1|33> scheduling rekeying in 85930s 2020-07-21 08:39:26 28[IKE] <Connection-Ipsec1|33> maximum IKE_SA lifetime 86290s 2020-07-21 08:39:26 28[ENC] <Connection-Ipsec1|33> generating ID_PROT response 0 [ ID HASH ] 2020-07-21 08:39:26 28[NET] <Connection-Ipsec1|33> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:39:26 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] 2020-07-21 08:39:26 03[NET] received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] on PortB 2020-07-21 08:39:26 03[NET] waiting for data on sockets 2020-07-21 08:39:26 07[NET] <Connection-Ipsec1|33> received packet: from X.X.X.X[500] to Y.Y.Y.Y[500] (652 bytes) 2020-07-21 08:39:26 07[ENC] <Connection-Ipsec1|33> parsed QUICK_MODE request 1475733680 [ HASH SA No ID ID N(INITIAL_CONTACT) ] 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> ### process_request invoking quick_mode_create 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> ### quick_mode_create: 0x7f2398001440 config (nil) 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> ### process_r: 0x7f2398001440 QM_INIT 2020-07-21 08:39:26 07[CFG] <Connection-Ipsec1|33> looking for a child config for Y.Y.Y.Y/32 === X.X.X.X/32 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> trying other candidates from phase 1 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> no matching CHILD_SA config found 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> queueing INFORMATIONAL task, already 0 tasks queued 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> flush_queue(IKE_NATD) 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> ### destroy: 0x7f2398001440 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> activating new tasks 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> activating INFORMATIONAL task 2020-07-21 08:39:26 07[ENC] <Connection-Ipsec1|33> generating INFORMATIONAL_V1 request 2863214840 [ HASH N(INVAL_ID) ] 2020-07-21 08:39:26 07[NET] <Connection-Ipsec1|33> sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500] (76 bytes) 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> activating new tasks 2020-07-21 08:39:26 07[IKE] <Connection-Ipsec1|33> nothing to initiate 2020-07-21 08:39:26 04[NET] sending packet: from Y.Y.Y.Y[500] to X.X.X.X[500]
This thread was automatically locked due to age.