Hello.
I'm posting this here to see if anyone else is experiencing this issue, and if it is possible to identify what exactly is going on with IPS on my XG Firewall.
It appears that with the most recent Windows Updates (KB4558998), when the update download reaches 99% in the Settings app, there are a huge number of IPS alerts generated (one of my firewall rules is scanning this particular traffic from all servers on my network to the Internet).
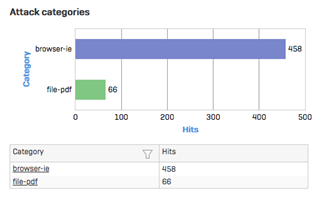
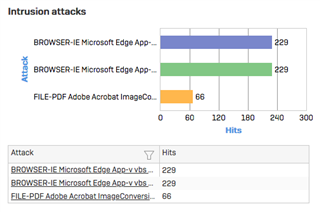
Here are the threats which are being detected:
BROWSER-IE Microsoft Edge App-v vbs Command
BROWSER-IE Microsoft Edge App-v vbs command attempt
I have had to temporarily disable the rule which permits access to Microsoft Services on my networks to stop the IPS alerts, because they continue constantly (as I assume Windows retries the download).
Some things to note:
- SSL inspection is enabled and configured on the Windows hosts
- XG Firewall version: SFOS 18.0.1 MR-1-Build396
- IPS signature version: 18.17.27
- This is occurring on all Windows Server 2019 devices, even freshly installed instances from an official ISO image in an isolated network.
- The IPS policy enforced by the firewall rule incorporates 'All Categories' (mainly for testing purposes).
Does this mean that the Windows Updates being downloaded contains actual malware signatures, or is it more likely to be a false positive?
Any advice or assistance would be appreciated. If more details are needed, please ask and I will supply them.
This thread was automatically locked due to age.