Good night.
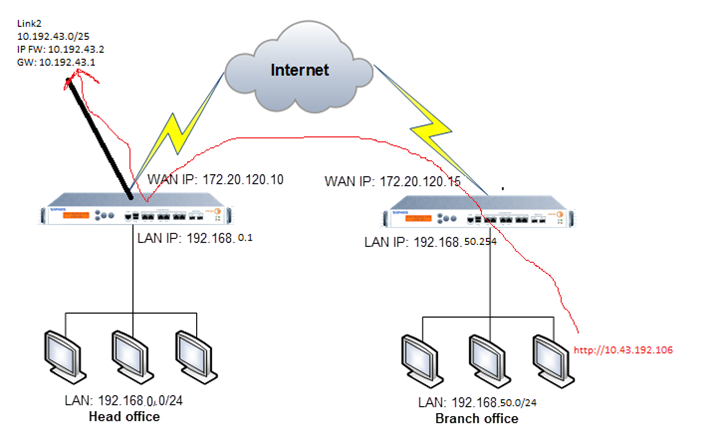
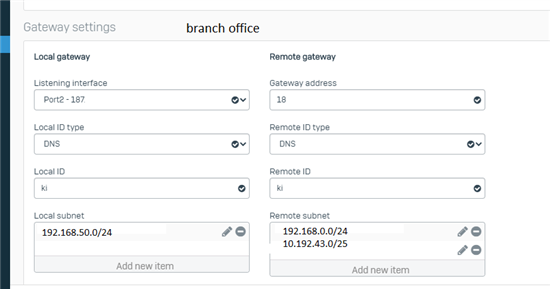
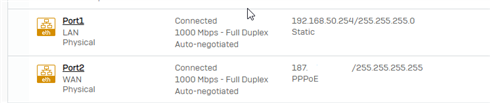
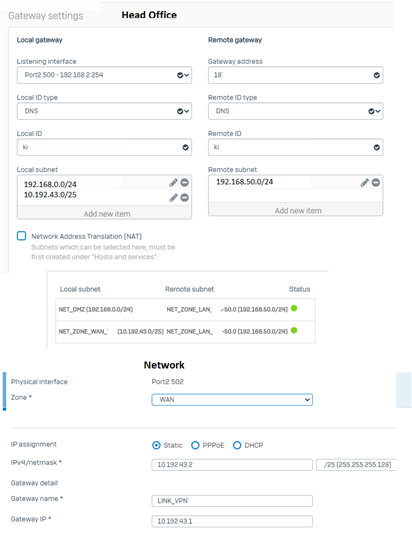
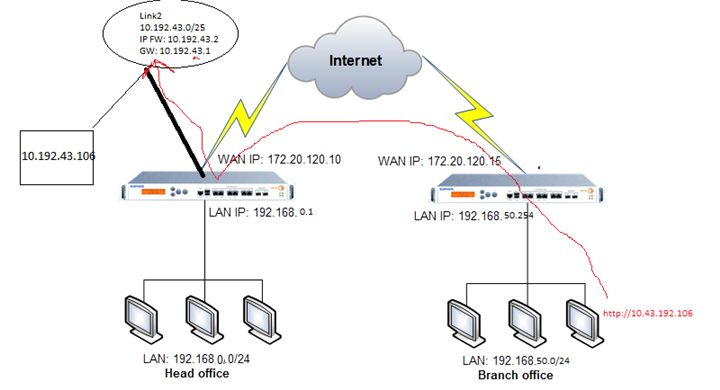
We have an IPSEC VPN between our branch and our headquarters.
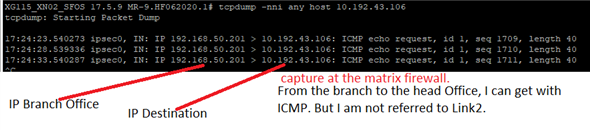
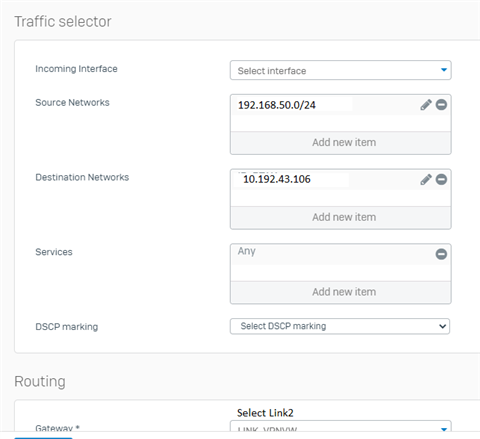
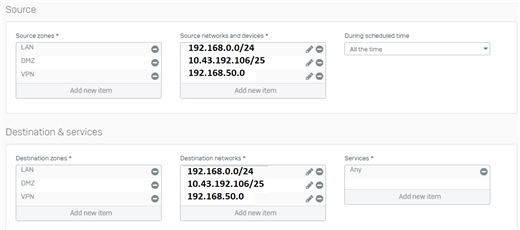
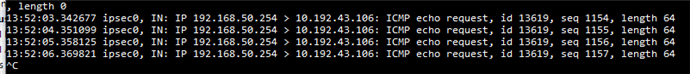
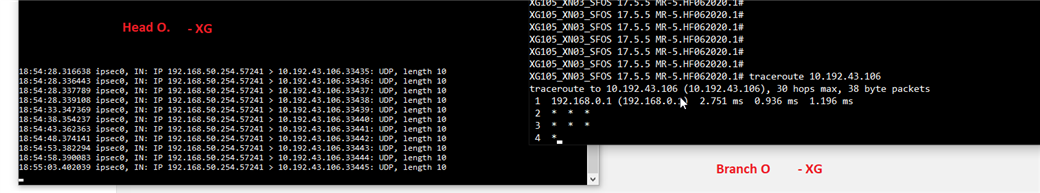
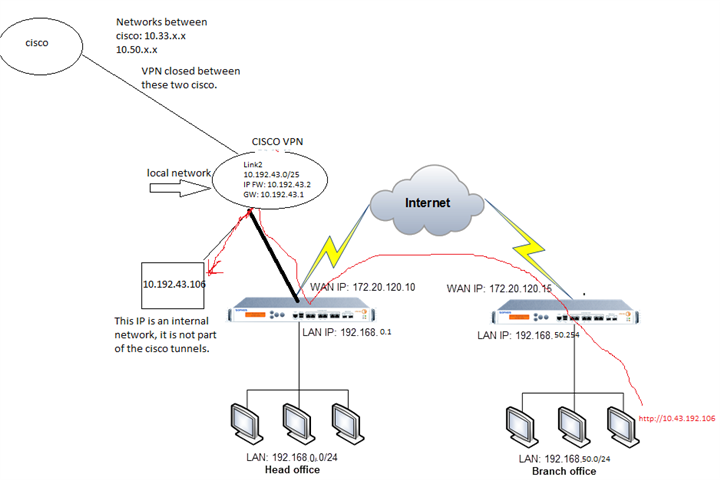
In our Branch, we need to access an IP address that is in a Link in our Headquarters. We managed to get to the headquarters, but we were unable to forward the connection to the link.
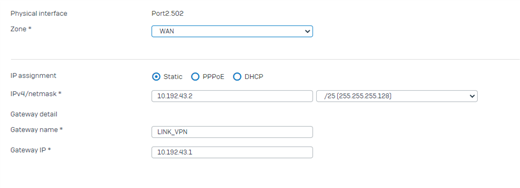
The branch accesses IP 10.192.43.106 which is in Link2 of the Headquarters.
I would like a suggestion on how to proceed in this case.
I followed what is in this topic but it didn't work: https://community.sophos.com/products/xg-firewall/f/network-and-routing/111938/site-to-site-vpn-and-static-routing
A topology of the environment follows.
This thread was automatically locked due to age.