Hello togehter,
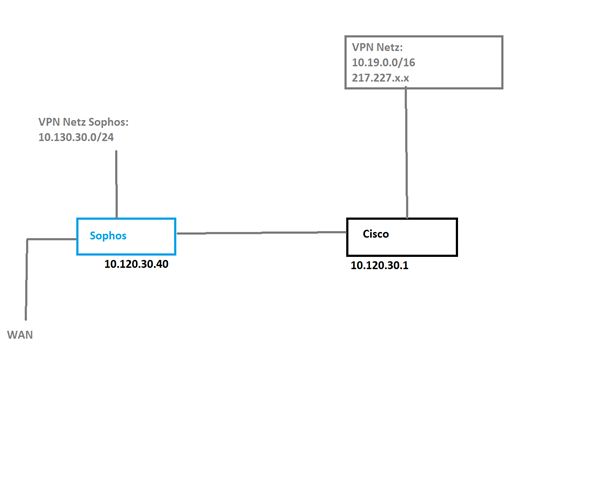
i have some trouble for routing in a ssl vpn tunnel. for some details i attached an image.
the ssl-tunnel routes every packet to the sophos - so it is configured as a standard gateway. if the vpn client open google.de the client break out at the sophos WAN-side (works as expected)
then i have an internal network (10.19.x.x)which is reachable via cisco router. okay there is a route and firewall rule which allows this - works also as expected.
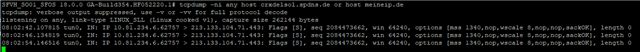
now i have a public IP (217.227.x.x) which must route via the cisco router. so i have a routing entry for that IPs. But nothing happened. I try to find out something with tcpdump and i saw that the traffic for that IP came in but there ist no outgoing packet. wether the sophos WAN or to the cisco Router.
I try to configure dedicated networks for the SSL-VPN settings and saw that this works. But it is mandatory for this constellation, that some public IPs (217.227.x.x) must reachable from the cisco side.
what i made worng?
thanks in advance
michael
This thread was automatically locked due to age.