Dear Team
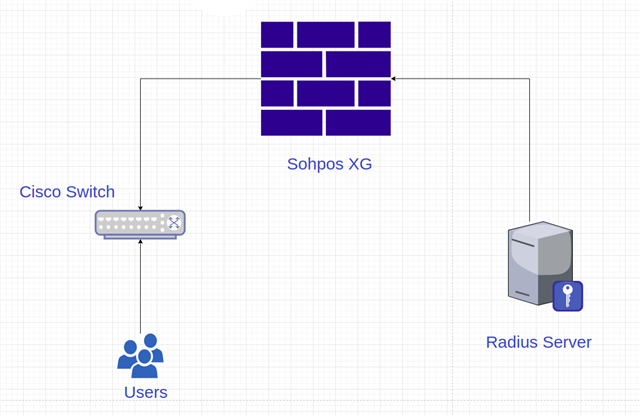
I have a topology like the diagram below and i need to use protocol 802.1x to auth users which connect to the switch from the radius server how can i do it .
Note the radius and switch in different subnets .
This thread was automatically locked due to age.