Hello
I'm new to sophos xg firewall. We have purchased XG210 to replace our ASA firewall.
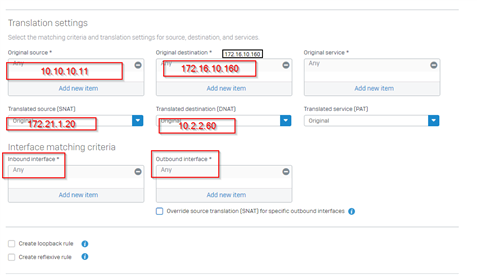
Most of the NAT rules on ASA are Twice NAT..Like this:
nat(inside,DMZ) source static OBJ-10.10.10.11 OBJ-172.21.1.20 destination static OBJ-10.2.2.60 OBJ-172.16.10.160
nat(inside,DMZ) source static OBJ-10.10.10.11 OBJ-172.21.1.20 destination static OBJ-10.2.2.66 OBJ-172.16.10.166
nat(inside,DMZ) source static OBJ-10.10.10.11 OBJ-172.21.1.20 destination static OBJ-10.2.2.61 OBJ-172.16.10.161
as you can see the first part (source static OBJ-10.10.10.11 OBJ-172.21.1.20) is the same for all rules but the second part is different.
How can I apply this on XG?
And another question: if i have a static 1 to 1 NAT rule like this
nat(inside,DMZ) source static OBJ-10.10.10.27 OBJ-172.21.1.33
On ASA: this rule (static NAT) allows bidirectional connection initiation, both to and from the host
I've defined a NAT rule in Sophos and specified the original IP, the translated IP, the inbound interface (LAN) and the outbound interface (DMZ)
so my question is: does this rule on Sophos allow bidirectional connection initiation same as in ASA?
Thank you very much in advance
Rana
This thread was automatically locked due to age.