Dear all,
in FOS17.5 we allowed access to the XGs webproxy on port 3128 by creating a firewall rule with allowing traffic from LAN to WAN with allowed service 3128 as documented in the following KB article: https://community.sophos.com/kb/en-us/125585.
After migrating to SFOS 18.0.0 GA-Build379 this does not work anymore. When a LAN client accesses the webproxy on port 3128, no website can be opened and the connction on the client times out. In the XGs logfile I can see the following:
1. Traffic from the LAN client to the webproxy (3128) is allowed
2. Traffic from the XGs WAN interface to the destination website is dropped
When adding HTTP & HTTPS in addition to tcp/3128 in the firewall rule everything is working fine - that however means, that transparent proxying is also allowed. To disable the transparent proxy, I need to create an additional firewall rule with allowing HTTP & HTTPS from LAN to WAN with Web Policy set to deny as mentioned in https://community.sophos.com/kb/en-us/132117.
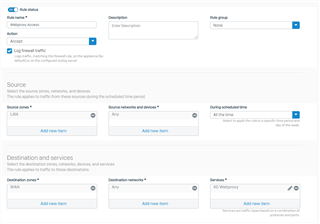
My firewall rule for allowing access to the webproxy looks like the following:
Is this behavior normal in FSOS18 because of the new drop rule at the end, so that in addition to tcp/3128 HTTPs & HTTPs always have to be explicitly allowed in the firewall rule as well?
Thanks
Michael
This thread was automatically locked due to age.