Dear all,
we're currently implementing an virtual XG 18.0.0 GA-Build379. The XG has one interface in the LAN zone with a private IPv4 address and one in the WAN zone with a public IPv4 address. I have read https://community.sophos.com/products/xg-firewall/f/recommended-reads/116102/understanding-new-decoupled-nat-and-firewall-changes-in-v18 and found out that even though in FOS18 there is a default drop rule #0 at the end, traffic matched by this rule is not being logged.
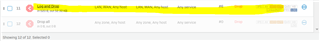
As I would like to have all dropped traffic being logged I created a new firewall rule set to log and drop and inserted it before the default rule: https://community.sophos.com/products/xg-firewall/f/recommended-reads/118125/sophos-xg-firewall-v17-5-how-to-log-all-dropped-traffic-without-interrupting-other-services
This works fine if i.e. the client 10.0.0.65 in the LAN zone tries to access service tcp/53 on host 8.8.8.8 in the WAN zone (which is not allowed by any other rule). In this case, traffic is being dropped and logged by the manually created drop rule (#6):
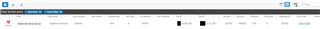
This is also reflected in the policy tester:
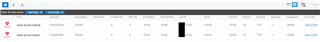
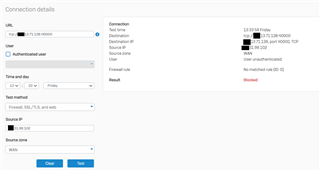
However, when trying to access the XG's WAN interface 172.13.71.138 on port tcp/40000 from another WAN host, traffic is being dropped and logged with rule name N/A:
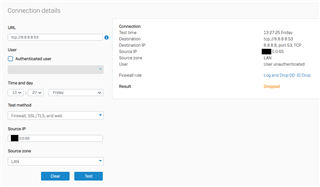
And in this case Policy Tester shows that no matched rule is found:
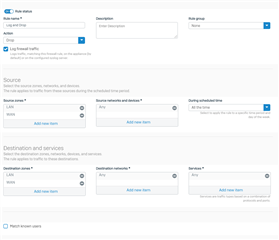
Shouldn't the manually created Log & Drop rule match in this case as well? Here's a details screenshot of my Log & Drop rule:
Or do I have to create a special rule in order to log blocked traffic from WAN hosts destined for the WAN interface of the XG?
Thanks
Michael
This thread was automatically locked due to age.