Good day guys
i have a Sophos Firewall XG 310, i upgraded form version 17.5 MR9 to version 18.0.379 due to security vulnerability..
in my time with version v17.5 i have no problem regarding all my config.. i have 2 DNAT rules 1 rule is for incoming WAN interface which doesn't have any masq, the other on above it is from incoming LAN interface which i put a masq..
there rules are for accessing public ip of the the hosted internal server..
bbackground: we do have blocks of public ip that that is natted on different local ip of servers
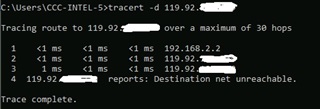
problem: in version 18.0.379 i've made 2 firewall rules, 1 is for LAN to public ip of out internal server..
SOURCE ZONE: any ,
SOURCE NETWORKS: the local subnet
DESTINATION ZONE: my local zone made
DESTINATION NETWORKS: the public ip of the server
then i made a DNAT which is working in when outside the network connecting to our server public ip,here is another DNAT for the internal trying to connect to out server public ip in the same network
Translated source (SNAT) : MASQ
This thread was automatically locked due to age.