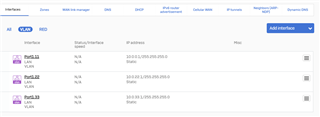
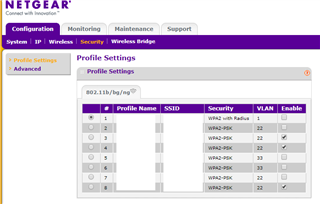
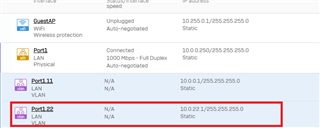
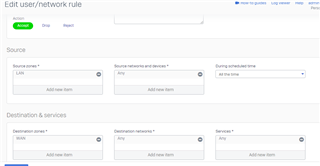
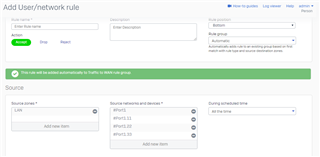
Running XG85, setup VLANs as such:
I have a wireless AP that assigns VLAN ID of 22, and on my managed switch, I set the port that connects the AP to the XG85 to Tagged (PVID=1).
While I'm able to connect to the AP, I'm not getting the ip set via DHCP on XG85.
What am I missing?
This thread was automatically locked due to age.