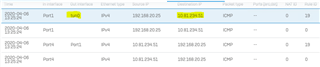
Manual notes the following, but WAN is not an option.
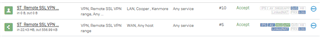
Check if an SD-WAN policy route has Destination networks set to Any.
Change the setting from Any to a specific choice (example: WAN) from the list. Setting it to Any forces XG Firewall to forward internal traffic also to the WAN interface.
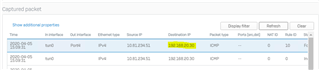
This seems like a very easy solution to my problem of all VPN SSL traffic appearing to try routing out the WAN interface.
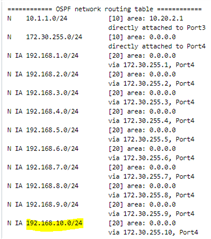
I am using OSPF routing for the network, and precedence is sd-wan. vpn, static, and I have no static routes.
Am I missing a workaround to the possible Any/Any issue?
This thread was automatically locked due to age.