Goal:
Create a single network between two remote locations accomplished by using two Sophos XG firewalls setup with RED connections using same subnet.
Requirements:
The restrictions of the of underlying devices (a DVR and cable Set-top-boxes) on this network require they all be on the same subnet and be able to freely pass/receive any broadcast messages across the subnet so as to discover and communicate with each other. This needs to occur across the local and remote locations.
Problem:
Simply put I have been unable to figure out how to successfully configure a seamless subnetwork where data and any broadcasted data is passed between the local and remote boxes. Known here out as box 1 and box 2
Here is the current setup:
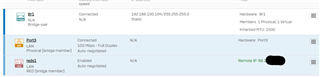
SFXGBox 1 – Verizon
XG Version – 17.5.10 MR-10
Port 1 – 192.168.1.x
Port 2 – Verizon (WAN)
_________________________
Bridge (Br0) – 192.168.100.103 (DHCP setup to serve requests on interface Br0)
Bridged Interfaces:
- Port 3 (Physical port)
- DVR – 192.168.100.112 – (DHCP successful)
- STB1 – 192.168.100.113 – (DHCP successful)
- reds1 – Firewall Red Server (online Spectrum IP displayed)
SFXGBox 2 – Spectrum
XG Version – 17.5.10 MR-10
Port 1 – 192.168.3.x
Port 2 – Spectrum (WAN)
_________________________
Bridge (Br1) – 192.168.100.115 (received DHCP from Box 1)
Bridged Interfaces:
- Port 3 (Physical port)
- STB2 – 192.168.100.xxx (unable to get DHCP from Box 1)
- Test PC – 192.168.100.xxx (unable to get DHCP from Box 1)
- reds1 – Firewall Red Client (online Verizon IP displayed)
BOTH XG BOXES HAVE FIREWALL RULES TO ALLOW LAN TO LAN TRAFFIC ANY SERVICES
More Info:
Each XG firewall has two independent networks defined under Port 1 on Box 1 & 2, (192.168.1.x & 192.168.3.x respectively) these are self-contained and are currently operating independent of each other and working as designed / expected – No changes needed or wanted here.
The common network I am attempting to create (192.168.100.x) between the two Sophos XG boxes is utilizing a RED site to site tunnel. I have successfully created the tunnel on each box (using Red Server / Red Client method) and they both show online; displaying the others WAN IP.
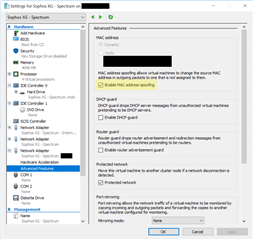
On Box 1, I have bridged the physical Port 3 and the reds1 (setup as RED SERVER) interfaces to create interface Br0 (both Port 3 and reds1 are in LAN zone) then set the static network as 192.168.100.103 /24, I have also selected “Enable routing on this bridge pair”.
On Box 1, I have setup a DHCP to serve requests on interface Br0 - 192.168.100.103 (to supply IP range 192.168.100.111 – 192.168.100.199 / 24) with DNS as 192.168.100.103
On Box 1, I have connected an external switch to Port 3 (Br0) and plugged in both my DVR and STB. Both devices successfully obtained an IP from the DCHP on Box 1, have internet access, and are both able to communicate with each other.
Here begins my problem
On Box 2, sticking with the same methodology, I have bridged Port 3 and reds1 (setup as RED CLIENT) interfaces to create interface Br1. (both Port 3 and reds1 are in LAN zone). Here instead of static network I choose DHCP, I have also selected “Enable routing on this bridge pair”.
On Box 2, the new bridge successfully receives an IP from DHCP on Box 1 and set as 192.168.100.115. (So here I can tell I have some communication between the two boxes but that is where it ends). I added another switch to physical Port 3 on box 2 and connected both the 2nd STB as well as a TEST PC to ensure the connection was working. Ignoring the 2nd STB at this point I’ve focused on the TEST PC to ensure I can get the basic network to function.
On Box 2, I attempted to pull an IP from the TEST PC connected to Port 3 on its bridged interface, I assumed it would work. I assumed wrong. I am getting no response from the DHCP on box 1.
Apart from playing around with different combinations of settings (completely stabbing in the dark). I seeking any assistance in how to get this setup to work. Maybe I’m on the right track or completely off course?
Noting: I have successfully followed the Sophos directions on how to setup an XG to XG RED but it was more aimed at connecting two different subnet. Which is not exactly what is needed here.
I am including a diagram of my current setup. The bit in the green box is what I am trying to create. The bit in the red box is the part that does not work.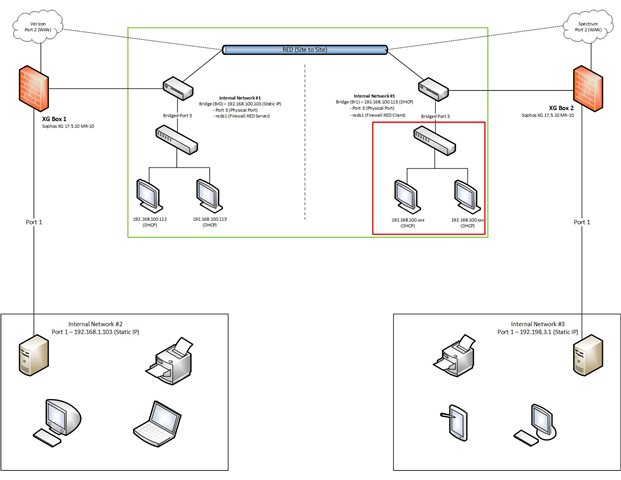
This thread was automatically locked due to age.