Hello Sophos Nerds
I recently configure a XG125 with (SFOS 17.5.9 MR-9) version as a replacement of X firewall ,
Every thing great but i have a trouble in a IPsec VPN connection with Cisco 800 Router
>>>>>
The Connection lost ( or Dropped ) after minutes "approx 30-60" from success connection established.
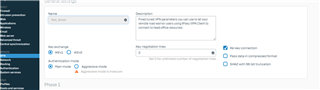
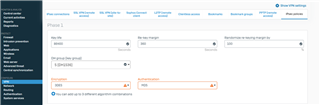
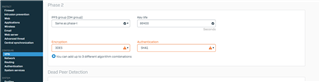
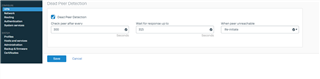
The Configuration of XG Firewall as :
The Configuration of Cisco 800 Router as follows :
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 5
crypto isakmp key zzz-psk address xxx.x.xx.xxx
!
!
crypto ipsec transform-set zzz-transformset esp-3des esp-sha-hmac
mode tunnel
!
!
!
crypto map zzz 10 ipsec-isakmp
set peer xxx.x.xx.xxx
set transform-set zzz-transformset
match address 110
No solutions by searching Google .
Can Any one give a suggestion
Thanks in Advance
Best Regards
Suliman
This thread was automatically locked due to age.