Hi,
I used to use Sophos XG as the DNS server in my network. Recently I setup pihole as my DNS Server for the entire network. In order to have all client use this as the DNS Server I changed the pushed DNS Server in all DHCP server in Sophos XG. For client with static IPs I did this manually.
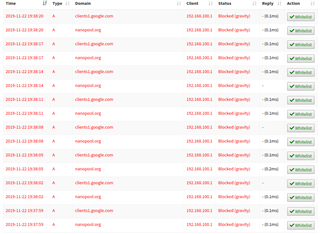
By the time the DHCP addresses are released and renewed most of the client use this DNS as it should be. However I still have thousands of DNS queries of 192.168.100.1 which is the Sophos XG Gateway and DNS server of one of my VLANs.
Is there any way to track down which client is still using the Sophos XG as DNS server and is the source for all these DNS queries.
This happens every second and assuming that both queries are from the same device, it looks like it is a Google something. However I have no idea which device this.
Any hints to find the source?
Best
This thread was automatically locked due to age.