Hey,
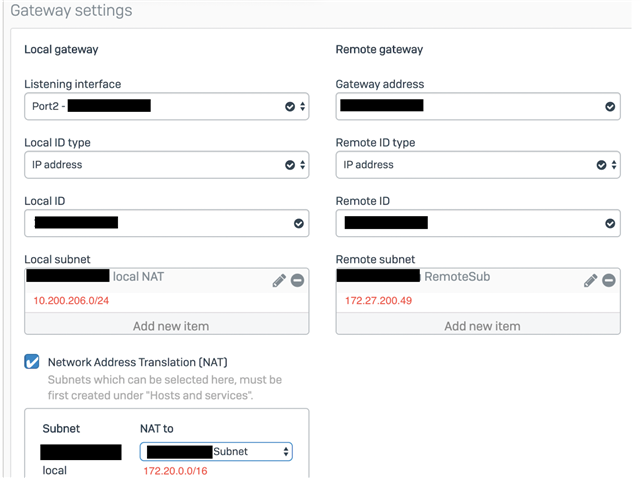
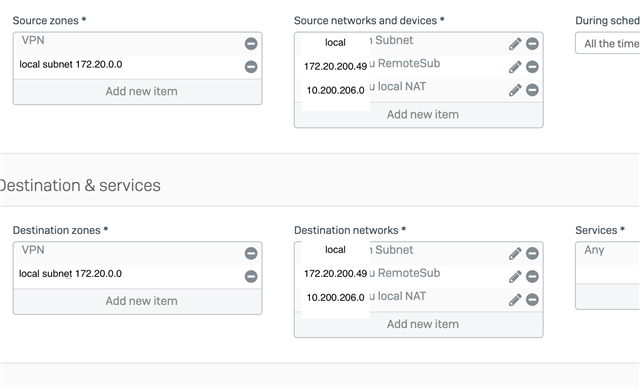
I would like to connect to a remote server via VPN. The s2s connection works but Iam unable to reach the server on the other side (the remote site is one host only).
I can see that the outgoing traffic goes through the firewall rule LAN to WAN, if I will connect from the local subnet 172.20./16 to the remote server 172.20.200.49.
So whats missing / wrong? Do I have to create a further rule/route - where ?
Thanks in advance!
This thread was automatically locked due to age.