Hi Guys,
SFOS 17.5.8 MR-8
STAS 2.5.0.
we currently have the situtation that users can not authenticate to the firewall via the STAS.
In the authentication Log via LogViewer we get the following error.
"User XXXXX failed to login to Firewall through AD authentication mechanism from 192.168.XX.XX because of wrong credentials"
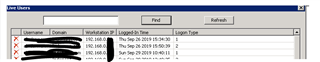
All users get get displayed on the stas via live users.
Even the connection between XG and STAS is working.
I would assume a problem on the AD server, but the login works if we log in with the AD user ID on the user portal.
Attached is a Part of the STAS log for a failed logon.
MSG [0x7a3c] 09.10.2019 07:48:11 : wrkstpoll_workerthread_wmi: logging on user '[DOMAIN]\TestUser' on '192.168.0.XX
MSG [0x7a3c] 09.10.2019 07:48:11 : wrkstpoll_handle_logon_req: Request received from CR
MSG [0x7a3c] 09.10.2019 07:48:11 : wrkstpoll_init_userinfo_common: CreateTime: 1570600091
MSG [0x7a3c] 09.10.2019 07:48:11 : wrkstpoll_init_userinfo_common: ExpireTime: 1570600696
MSG [0x7a3c] 09.10.2019 07:48:11 : wrkstpoll_init_userinfo_common: LogonType: 1
DEBUG [0x7a3c] 09.10.2019 07:48:11 : dca_filter_by_username
DEBUG [0x7a3c] 09.10.2019 07:48:11 : userdb_handle_duplicate_userinfo: select query: SELECT * FROM UserInfo WHERE wrkst_ip=='192.168.0.XX';
DEBUG [0x7a3c] 09.10.2019 07:48:11 : userdb_insert_userinfo: no matching userinfo found
DEBUG [0x7a3c] 09.10.2019 07:48:11 : userdb_insert_userinfo: UserInfo Successfully Inserted
MSG [0x7a3c] 09.10.2019 07:48:11 : wrkstpoll_handle_logon_req: new userinfo added
DEBUG [0x7a3c] 09.10.2019 07:48:11 : list_add_tail: first element added
DEBUG [0x7a3c] 09.10.2019 07:48:11 : wrkstpoll_handle_logon_req: user logon request enqueued to XG Update Queue
ERROR [0x5444] 09.10.2019 07:48:11 : USERINFO WAITING INFINITE
DEBUG [0x5444] 09.10.2019 07:48:11 : list_remove_head: last element removed
MSG [0x5444] 09.10.2019 07:48:11 : SSOclient_thread: got userinfo: USER: domain.com\TestUser <-> Flags: 5
DEBUG [0x5444] 09.10.2019 07:48:11 : SSOclient_filter_CR_subnet: Entering filter function
DEBUG [0x5444] 09.10.2019 07:48:11 : SSOclient_filter_CR_subnet: authnet not specified, send request to XG
ERROR [0x5444] 09.10.2019 07:48:11 : SSOclient_update_CR: domain name is there with length 13 , domain.com
ERROR [0x5444] 09.10.2019 07:48:11 : USERNAME TestUser Length 5
ERROR [0x5444] 09.10.2019 07:48:11 : WORKSTN IP 192.168.0.XX Length 13
ERROR [0x5444] 09.10.2019 07:48:11 : DOMAIN domain.com Length 14
ERROR [0x5444] 09.10.2019 07:48:11 : SSOclient : PACKET SIZE 243 㐲3
DEBUG [0x5444] 09.10.2019 07:48:11 : net_send: bytes sent: 243
DEBUG [0x5444] 09.10.2019 07:48:11 : net_send: full packet sent
MSG [0x5444] 09.10.2019 07:48:11 : SSOclient_thread: Logon/Logout Update sent to: 192.168.0.XX
ERROR [0x5444] 09.10.2019 07:48:11 : GETTING (USERINFO) FROM QUEUE
DEBUG [0x5444] 09.10.2019 07:48:11 : list_remove_head: list is Empty
DEBUG [0x7a3c] 09.10.2019 07:48:11 : threadpool_finishnotify: Thread ID: 0x7a3c
DEBUG [0x7a3c] 09.10.2019 07:48:11 : threadpool_finishnotify: Reset Event
What else could be the cause ?
Kind Regards,
Max
This thread was automatically locked due to age.