This week I jumped from a typical consumer grade box to an XG 125 running a home license. So far so good, but I'm new to Sophos (and more advanced firewall applications in general).
My goal has been:
- A security focused device with long term firmware support (Check)
- Allow all devices on the LAN to access to the Internet/WAN (Check and working)
- Make sure devices on the LAN are behaving (AV & some APP Rules. Done and Working)
- Country Block Rules (Check, working?)
- Similar to my consumer router LAN to WAN is ok. WAN to LAN is bad, unless something on the LAN requested it.
- Keep an eye on what LAN side devices are requesting, something I wasn't able to do previously (Check and eye opening)
- Lateral Movement protecting for a few devices on my network (Not yet setup, but the process seems straight forward).
- No remote access / VPN for the moment (Done, port 443 and user portal, disabled).
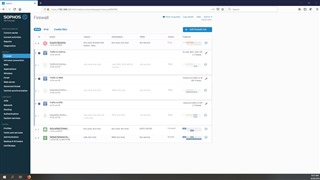
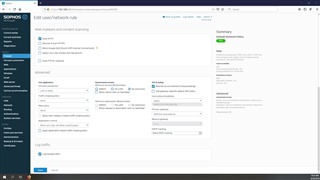
Screenshots of my current, simple setup:
I mean, is that it? It seems so simple. My concern here is the default Allow (ID 5) I've configured isn't setup correctly. All of my IOTs, the NAS, Laptops, Computer, Tablets, Phones etc are all working as they did before. Nothing is wrong...setup was simple. Where is the complication, the allow ports/services etc one by one?
Should I instead deny everything, watch everything go down and then open services/ports until everything is working again (and by this method, will end up blocking anything that is not used?)
The biggest weakness here, isn't Sophos, but rather an inexperienced firewall user unsure if best practices are being followed.
This thread was automatically locked due to age.