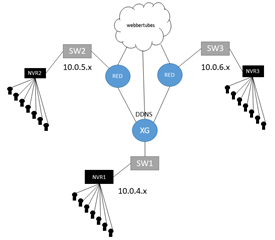
Wondering if anyone can help me out.
Trying to configure remote access to some NVRs at some branch locations connected via split tunnel to an XG135 at HQ. I have the NVR at HQ working fine using Sophos DDNS - easy enough - but can't figure out to configure/how to configure the REDs for their own DDNS (since they access the internet directly). I have no need nor desire to route the cam traffic through the XG but am willing to try it if I have to. Any info appreciated.
Pardon the crude PP drawing. The direct connects to the internet from REDs is supposed to represent the split tunnel - I'm sure you get it.
This thread was automatically locked due to age.