Ho Community,
i'm just a little helpless about the following scenario on an XG firewall (current firmware).
Requirement
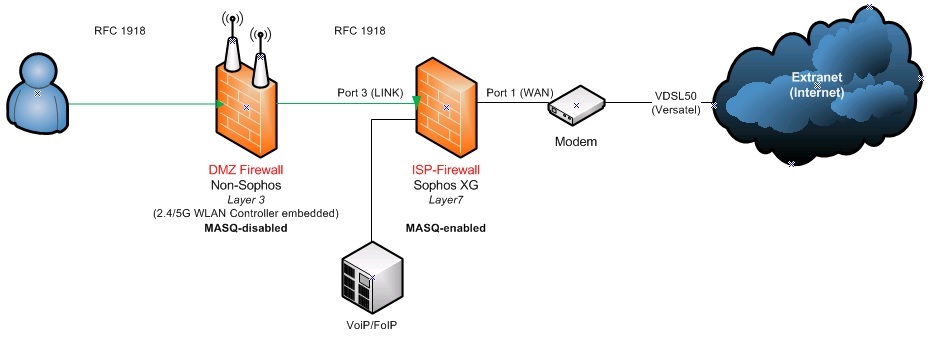
Android devices connect via OpenVPN to the XG firewall, which is directly connected to the ISP (no problems).
The destination devices are located behind a internal Firewall/WLAN-Controller.
Situation
The devices can communicate with the XG via the port of the FW/WLC without any problems and also access the Internet.
From XG to internal FW/WLC is a seperate vLAN in production.
The internal FW/WLC has routing sets, to forward the vLAN's without any NAT directly to the XG Firewall to forward them to the internet (NAT on the XG).
If a Android device is successfull connected to XG (SSL VPN) connection successfull - it's not possible to reach a device, that is behind the internal FW/WLC.
Routeing configuration fpr all vLANs are correctly on the XG firewall.
Reconfigure the routing (static dynamic) trough console command dose not fix the issue.
My Problem
If the Android device is connected trough SSL VPN to XG Firewall, the XG send no package to the internal Firewall (logging internal FW trough wireshark).
- VPN to LAN (MASQ) is also not the solution ;(
- Set routing to static route for VPN -> nothng changed.
Question
Any idea hwo to send requests from the XG trough port3 to the internal Firewall/WLC device during a SSL VPN connection.
ASCII (from external to internal destination)
Extranet ----> SSL VPN (XG Firewall at Port1) --- VLAN0005 (port3) ---> FW/WLC (Port 1) ----> VLAN0070 ----> FTP Service / HTTP Web Interface.
Any idea what's wrong or a example what to check to get connected ?
thanks forward and regards
Chris
This thread was automatically locked due to age.