Hi all,
I'm still a rookie when it comes to this beast of a product so please bear with me.
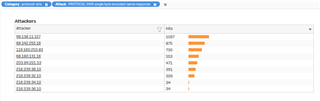
I'm seeing a lot of "PROTOCOL-DNS single byte encoded name response" attacks and they all originate from Yahoo and Google name servers.
My question is 3 parts, why, what does it mean and how can i stop it?
I have Sophos XG running as a VM with a single NIC configured as passthrough so the XG can connect directly to the web using PPPoE. On the LAN side i have Pi-Hole running with Unbound is configured to use Root Name Server.
Pi-Hole is the DHCP and DNS server for the network. Clients point diectly at Pi-Hole for DNS queries. The XG points at the Pi-Hole for DNS queries too.
I don't have a problem with DNS resolution, it works well. I just don't like seeing attacks and would like to understand whats going on and prevent it if possible.
This screenshot shows the sheer number of "attacks". It seems like a LOT considering the XG has only been in place for around 18 hours.
This thread was automatically locked due to age.