This is a peculiar one, as I have had this Cisco SG200-26 switch working with a Juniper SRX110HA-V2.
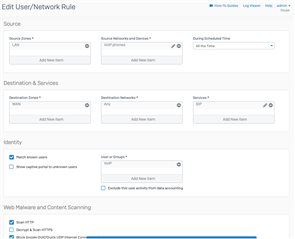
Topology is pretty straightforward: Three VLANS (IDs 3, 4 and 5) are required. The XG86 has these three VLANs configured on LAN port 1 (Port 1.3, 1.4 and 1.5). LAN port 1 is connected to port 24 of SG200, with port 24 configured as a Trunk with Tagged modes for VLAN IDs 3, 4 and 5 accordingly.
The only device that seems to function is the only one that can support tagging (its port is configured as Trunk - Tagged for VLAN ID 5). All other devices are not capable of supporting VLAN tagging, so their ports are set up as Trunk with Untagged mode for VLAN ID 3 or 4 (as required). In the very least, all the untagged devices do receive their address assignments from their respective DHCP servers (configured in the XG, not external) but that's where it ends.
If I plug a computer directly into Port 3 of the XG, which I have configured with a static IP belonging to the VLAN 3 group, I can ping all three VLAN gateways/interfaces but not any of the VLAN 3 devices themselves. However, I am able to ping the VLAN 5 device I mentioned.
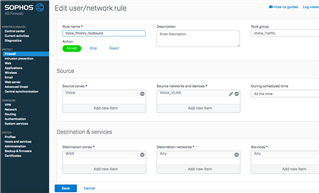
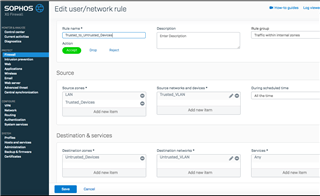
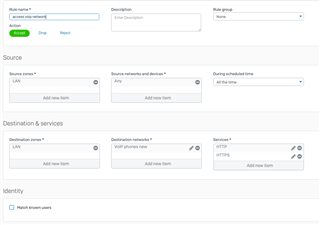
I'm using the same Firewall rules as the VLAN 5 zone, so I know it can't be the rules since the same parameters work for the VLAN 5 tagged device.
As I mentioned at the start, this switch configuration definitely works with the Juniper but it seems that the XG only seems to work for the one device capable of VLAN tagging.
So the question is, which one is breaking protocol concerning 802.1q? Is it the XG or the SG200? I'm inclined to blame the XG86 for this, given that is the only thing that has changed here. I've sought out all the experts' videos on YouTube showing how easy it is to set up VLANs (and I agree they are easy) but there's something horribly wrong here.
I am running the latest version SFOS (17.5.6).
All help appreciated!
This thread was automatically locked due to age.