Hallo,
ich bin am Verzweifeln. Ich bekomme nach dem Herstellen einer SSL-VPN Verbindung keinen Zugriff auf mein Webadmin der SG.
Eigendlich sollten ja die FW Einstellungen automatisch erfolgen. Kann es mit mit dem Web Protection oder WAF zusammen hängen. P.s. Auf alle anderen Geräte wie Switche, NAS, Router etc. komme ich nur nicht auf das Admin WebInterface der Sophos SG
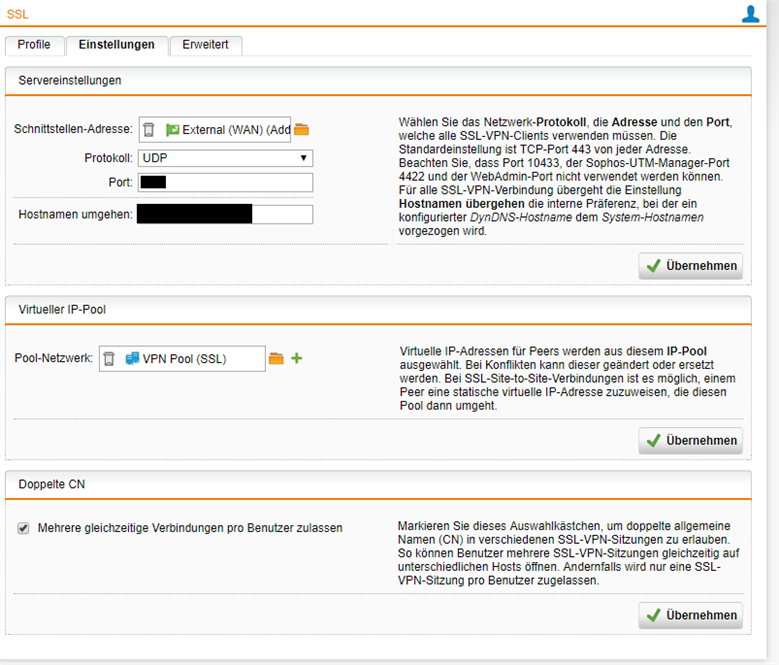
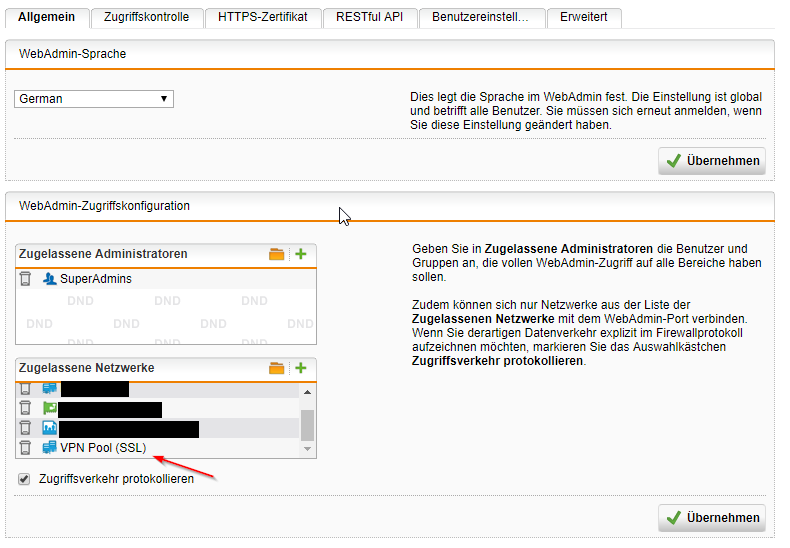
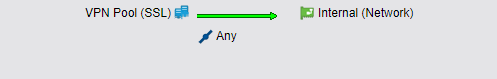
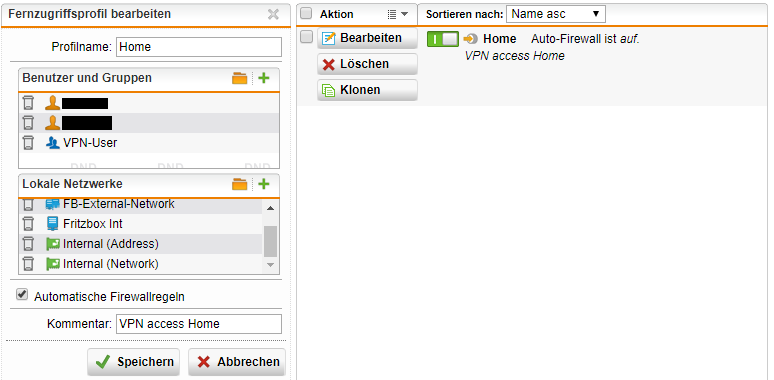
Hier die Config was ich habe
This thread was automatically locked due to age.