Hi folks,
Could someone has ideia if is it possible create a RED VPn between XG devices using multiple WAN interfaces in Branch and Head office ?
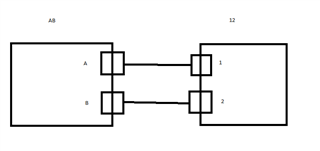
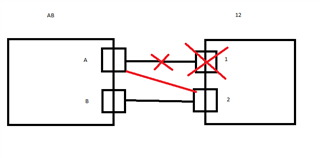
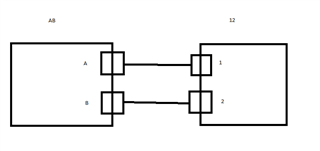
eg.
H.O WAN 1 ---------------RED TUN 1---------------------------- B.O WAN 1
H.O WAN 1 ---------------RED TUN 2---------------------------- B.O WAN 2
H.O WAN 2 ---------------RED TUN 3---------------------------- B.O WAN 1
H.O WAN 2 ---------------RED TUN 4---------------------------- B.O WAN 2
Best regards
Carlos
This thread was automatically locked due to age.