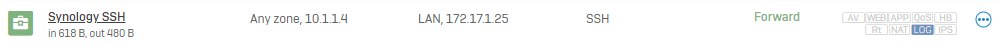
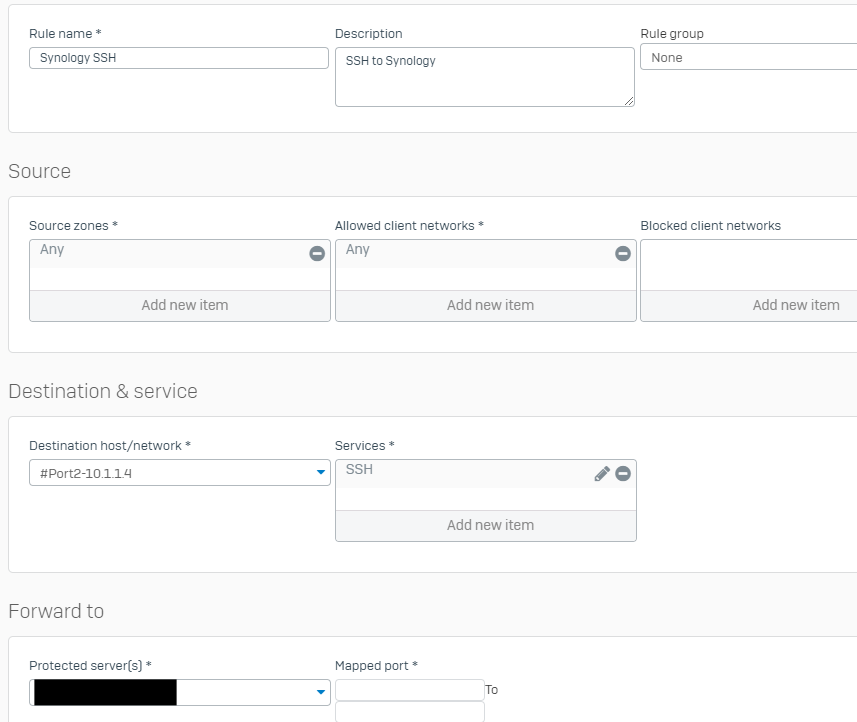
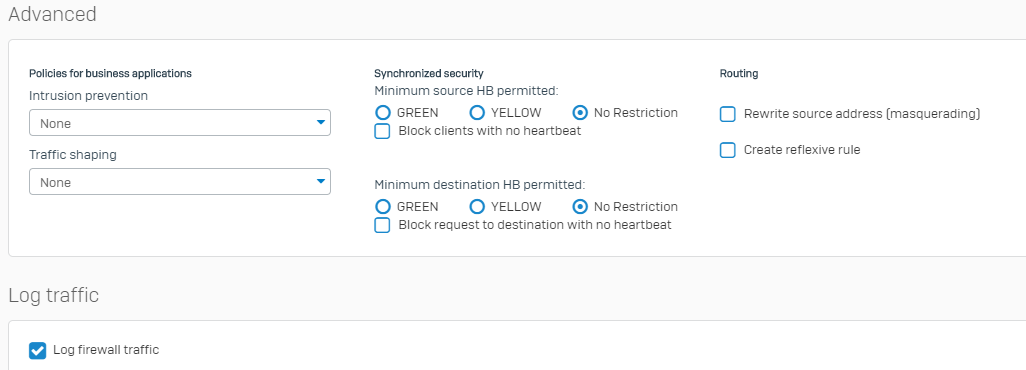
Trying to setup a basic port 22 forwarding to a Synology NAS unit, and unfortunately not having any luck.
Basic info:
Port #2 is the WAN of course, Protected server is the hostname/IP (172.17.1.25) of the Synology NAS. Mapped port is blank - won't accept any input, since I'm using the designated SSH service above.
Advanced:
Tried with/without MASQ, port 22 still shows as Closed to external attempts.
Do I have to do something else somewhere in order for the firewall rule to work, or am I missing something?
This thread was automatically locked due to age.