Hi @ all,
short story: I uploaded via API/CLI succuessfully a certificate to XG, changed it in webadmin but i have now trouble in firewall to change it in my WAF-rules. Please help me to archive this. The issue I have seems buggy or undocumented, because there are in API-Documentation no parameters for "SourceNetworks" and "ExceptionNetworks". That question should create clarity.
The field I'm going to change is the following: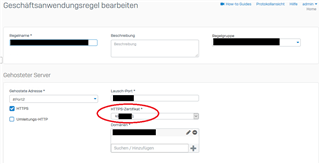
long story:
I got a python-script, which allows me to upload my pfx-certificate to my XG (thanks to Sophos-team):
#!/usr/bin/env python
import requests
import urllib3
urllib3.disable_warnings()
MY_CERT = 'C:\\folder\\folder\\mycert.pfx'
APIURL = 'https://my.sophos.xg:4444/webconsole/APIController?'
APICall = """<Request><Login><Username>admin</Username><Password passwordform="plain">XG_password</Password></Login><Set operation="add"><Certificate><Action>UploadCertificate</Action><Name>test01</Name><CertificateFormat>pkcs12</CertificateFormat><CertificateFile>mycert.pfx</CertificateFile><PrivateKeyFile></PrivateKeyFile><Password>PFX_password</Password></Certificate></Set></Request>"""
XGREQUEST = {'reqxml' : (None, APICall)}
XGREQUEST ['mycert.pfx'] = ('mycert.pfx', open(MY_CERT, 'rb'), 'application/octet-stream')
r = requests.post(APIURL, files=XGREQUEST, verify=False)
After that script the certificate appears correctly in webbrowser.
Now I got a second python-script whichs allows me to fire pre-written XML-files against my XG. The nice part: it returns the answer from XG. Together with the apiparser.log its a nice debugging-tool (thanks to Sophos-community):
#!/usr/bin/env python
import requests
import urllib3
urllib3.disable_warnings()
xml_files = ['C:\\folder\\folder\\myFile1.xml', 'C:\\folder\\folder\\myFile2.xml'] # Add xml files here
ip_address = 'ip.of.the.XG'
def api_call(api_ip, xml_doc):
api_url = r'https://{}:4444/webconsole/APIController?'.format(api_ip)
payload = {'reqxml' : (None, open(xml_doc, 'rb'))}
r = requests.post(api_url, files=payload, verify=False)
print(r.text)
for file in xml_files:
api_call(api_ip=ip_address, xml_doc=file)
The first XML-file changes the certificate in webadmin of the XG. The name of the cert is "test01", which comes from the upper script.:
<Request APIVersion="1702.1">
<Login>
<Username>admin</Username>
<Password passwordform="plain">XG_password</Password>
</Login>
<Set>
<AdminSettings transactionid="">
<WebAdminSettings>
<HTTPport></HTTPport>
<HTTPSport>4444</HTTPSport>
<UserPortalHTTPSPort>443</UserPortalHTTPSPort>
<Certificate>test01</Certificate>
<PortalRedirectMode></PortalRedirectMode>
<PortalCustomHostname></PortalCustomHostname>
</WebAdminSettings>
</AdminSettings>
</Set>
</Request>
But now is coming the XML which doesn't work, I want to change in a WAF-rule my certificate which I uploaded earlier.
I think in API its a HTTPBased-policy, because the named parameter-fields are the closest to the XG-webinterace, but I don't know really.
There are many mentioned but empty fields in one handy because the apiparser.log misses them and in the other handy they are mandatory, but currently I'm still in the script building content:
<Request APIVersion="1702.1">
<Login>
<Username>admin</Username>
<Password passwordform="plain">XG_password</Password>
</Login>
<Set>
<SecurityPolicy transactionid="">
<Name>name_of_my_rule</Name>
<Description></Description>
<Status></Status>
<IPFamily></IPFamily>
<isenable></isenable>
<Position></Position>
<PolicyType>HTTPBased</PolicyType>
<SourceNetworks>
<Network>something_needed_to_be_here</Network>
</SourceNetworks>
<ExceptionNetworks>
<Network>something_needed_to_be_here</Network>
</ExceptionNetworks>
<HTTPBasedPolicy>
<!--HTTP base policy is only applicable for IPv4-->
<HostedAddress></HostedAddress>
<HTTPS></HTTPS>
<RedirectHTTP></RedirectHTTP>
<ListenPort></ListenPort>
<Domains>
<Domain />
</Domains>
<ProtocolSecurity />
<CompressionSupport></CompressionSupport>
<RewriteHTML></RewriteHTML>
<RewriteCookies></RewriteCookies>
<PassHostHeader></PassHostHeader>
<Certificate>test01</Certificate>
</HTTPBasedPolicy>
<IntrusionPrevention></IntrusionPrevention>
<TrafficShapingPolicy></TrafficShapingPolicy>
</SecurityPolicy>
</Set>
</Request>
The following response I get if I leave the red marked parameters empty (so the white text does not exist, only the black one):<?xml version="1.0" encoding="UTF-8"?>Picture of XG-LOG:
<Response APIVersion="1702.1" IPS_CAT_VER="1">
<Login>
<status>Authentication Successful</status>
</Login>
<SecurityPolicy transactionid="">
<Status code="501">Configuration parameters validation failed.</Status>
<InvalidParams>
<Params>/SecurityPolicy/SourceNetworks/Network</Params>
<Params>/SecurityPolicy/ExceptionNetworks/Network</Params>
</InvalidParams>
</SecurityPolicy>
</Response>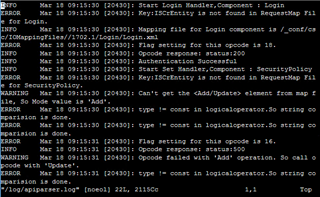
I get the following response if I enter any of the red marked parameters (because I do not know, what exactly I have to enter):<?xml version="1.0" encoding="UTF-8"?>
<Response APIVersion="1702.1" IPS_CAT_VER="1">
<Login>
<status>Authentication Successful</status>
</Login>
<SecurityPolicy transactionid="">
<Status code="501">Configuration parameters validation failed.</Status>
<InvalidParams/>
</SecurityPolicy>
</Response>
Picture of XG-LOG: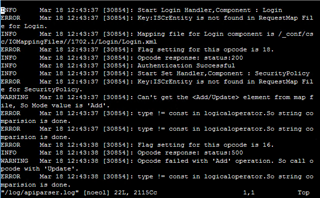
Perhaps you may see that the logs say the same - you are right :-)
That's why I show you the XML-files and scripts ;-)
Please help me to change the xml correctly.
greetings
This thread was automatically locked due to age.



