Hi all!
I need to block a few sites and the easiest way is to use wildcarded FQDNs. I've configured a block rule and added FQDN Group as target. Then noticed that the rule won't apply at all.
The rule with *.targetdomain.com target won't be blocked. I need to add all the subdomains exactly like mail.targetdomain.com and targetdomain.com, etc.
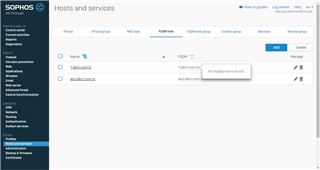
Tha main reason is that the DNS list of wildcarded domain is empty:
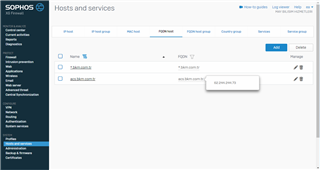
In real there are subdomains including the domain's itself:
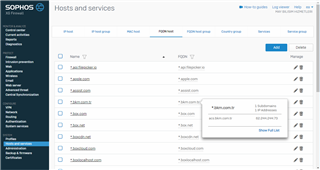
After a while the subdomain has been resolved. The domain still non-exist:
I also noticed you cannot modify FQDN if it has wildcard. It seems like a bug to me.
My unit is XG135 (SFOS 17.5.3 MR-3)
Is it a good way to block targets using wildcarded FQDNs? The best way would be using IP addresses to block. However FQDNs are the easiest, especially wildcarded ones.
This thread was automatically locked due to age.