Hi
We are running a centralized TACACS+ Infrastructure, which we use for admin login to our customer network devices.
This works perfect for Sophos UTMs, Cisco ASA, Cisco Switches, routers and almost all TACACS+ capable devices but not with Sophos XG.
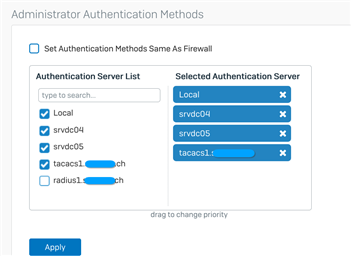
On the XG we've added the TACACS+ Server, tested the connection and set the administator authentication methods, so that it authenticates user against the TACACS Servers.
The problem is, that the XG prevents unknown TACACS+ user from login to the Webadmin, although it does reach out to the TACACS+ server and a permit is sent back.
After troubleshooting I found out, that the problem is because if the user connects for first time to the Webadmin it only has "user privileged" and thus is not allowed to login, nor is locally created.
The only way to achieve admin login via TACACS+ is:
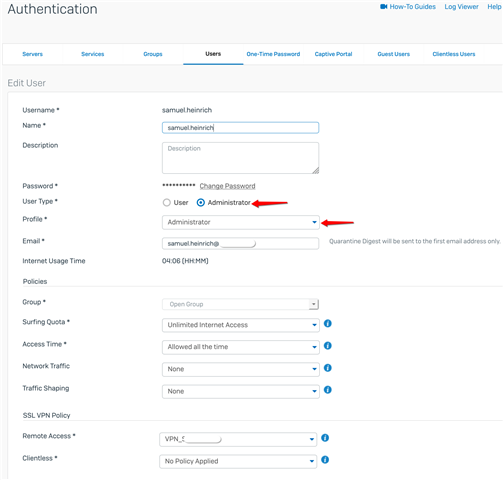
- Login via User Portal with TACACS+ Credentials, so that the user is created locally
- Manually assign Administrator Profile to the TACACS+ user
- Manually set User Type to Adminstrator
unfortunately this is not very scaleable and very undynamic.
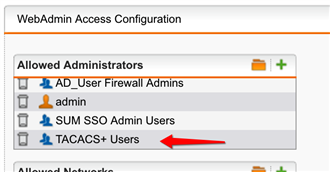
On the UTM as soon as you add external TACACS+ Server there is a Group object "TACACS+ User" which you can directly link to Webdmin Login, this way TACACS User don't need to be created on the firewall first, only if they need additional services like sslvpn etc.
I totally understand the the XG has a different approach in the way how it treats user, roles and group and that is good, but it would be nice to have to ability to somehow have tacacs user login directly to the webadmin. Eg:
- Ability to create a group for tacacs user and automatically assign admin privileges to new tacacs user
- Ablity to pre create "TACACS+" Type Users via CSV Import or SFM.
Btw. As far as i can tell, the same issue happens with Radius
open for any comments.
Cheers
This thread was automatically locked due to age.