Hi,
I've configured an Azure VPN with XG210, but the connection with one local vlan failed.
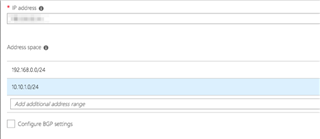
AZURE VNET: 172.16.0.0/16
AZURE SUBNET: 172.16.205.0/24
LOCAL SUBNET: 10.10.1.0/24
messageid="18060" log_type="Event" log_component="IPSec" log_subtype="System" status="Failed" user="" con_name="Vpn_AZURE-1" con_type="0"
src_ip="##.##.##.##" gw_ip="" local_network="10.10.1.0/24" dst_ip="##.##.##.##" remote_network="172.16.205.0/24"
additional_information="" message="Vpn_AZURE-1 - the received traffic selectors did not match: 172.16.0.0/32 === 10.10.1.0/24 (Remote: ##.##.##.##)"
In occasions de vpn get connected but suddenly get disconnected.
Any help?
This thread was automatically locked due to age.