Hi,
Due to the lack of any support for multicasting (IGMP Proxy), I'm forced to do it by myself.
I have changed from a UTM 9 based firewall and are used to use any other kind of firewalls, but XG has really re-invented the wheel. With other words I'm a bloody beginner with a XG based firewall. Even simple rules / policies are like rocket science until the point the admin gets the idea behind the "new" way.
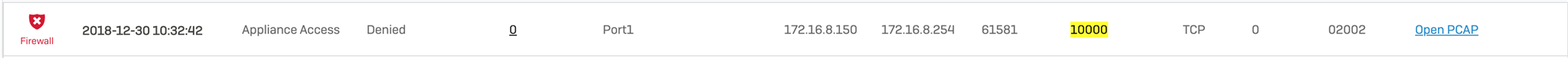
I'm running a custom service on the XG firewall (UDPXY) and that one is bound to TCP port 10000 (http traffic). The log output of the UDPXY mention, that creating the socket has been done successfully. But every try to access this services will fail because it's going to be blocked by the firewall.
Then I tried to create a new rule "Protect -> Firewall -> New User / Network Rule". I tried different combinations, but the simplest one with "any any" and only specifying the port (tcp 10000) does not work either.
Then I saw there is a configuration section called "System -> Administration -> Device Access -> Local Service ACL Exception Rule". But in here I can only add services which are predefined and covers the basic services offered by XG itself.
Any idea how to work around? If the product managers follows tightly the idea of future administrators are kids (I guess this is the direction they develop the XG product, not for professionals), then only applying custom iptable rules will help. But I really hope I have not to do this!
Thank you guys!
Cheers Danny
This thread was automatically locked due to age.