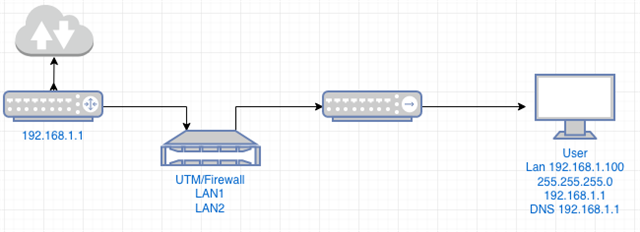
Hallo Zusammen,
ich habe mal eine Frage
ist es möglich die utm zw ein netzwerk zuhängen als real time Virenscanner
(internet verkehr )
ohne etwas am router oder an den cleints zu ändern siehe Bild
Vielen Dank im Voraus
This thread was automatically locked due to age.