Hallo liebe Community,
aktuell habe ich ein kleines Problem mit SFOS 17.5.0 und dem IPSec Conect Client. Ich kann mich erfolgreich mit dem Sophos Connect Client über IPSec mit der Appliance verbinden, komme aber leider nicht in das Interne LAN sowohl mit IP oder DNS.
Über ipconfig /all wird mir beim Tunneladapter eine IPv4 adresse in einem 10.xxx.xxx.xxx/32 zugewiesen OHNE Standartgateway!
Ich würde gerne auf meine internen Ressourcen zugreifen aus dem LAN, habe ich eine Einstellung vergessen?
XG:
WAN:PPPoE
LAN:172.17.10.0/24
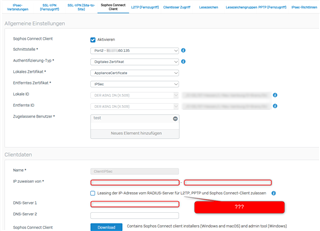
Sophos Client IPsec Konfiguration:
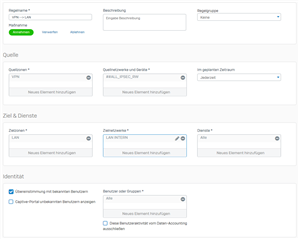
Firewall Regel:
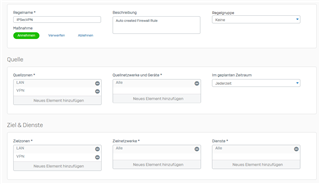
alternative Firewall Regel, geht auch nicht...
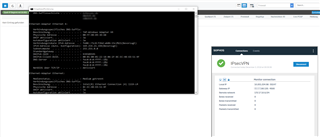
IPsec Verbindung:
This thread was automatically locked due to age.