I have created a new rule set and added everything that matches SSH but still I do see people trying my SSH server:
Nov 12 10:18:34 bananapi root: DENY sshd connection from 193.33.8.98 (PL)
Nov 12 10:18:34 bananapi sshd[32506]: aclexec returned 1
Nov 12 10:18:34 bananapi sshd[32506]: refused connect from 193.33.8.98 (193.33.8.98)
I have the following rule set for the SSH port forward firewall rule:
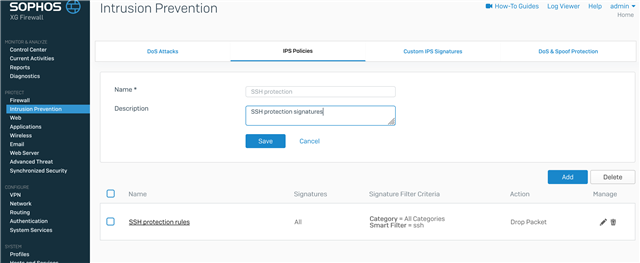
How can I block SSH scan attempts or why are scan attempts continuing through the IPS rules?
This thread was automatically locked due to age.




