Hello!
I'm using a DNS content filtering service (Clean Browsing) and am trying to specify different DNS servers for different zones so that different DNS filtering policies are applied by setting the DNS servers in each specific zone's DHCP settings and then allowing only those DNS servers through via a firewall rule. Clean Browsing allows you to create profiles with different DNS filter categories and generates new DNS server IPs for each specific profile. So clients pointing to Clean Browsing's DNS Server IP A from my WAN address get a different DNS filter policy than those pointed at DNS IP B
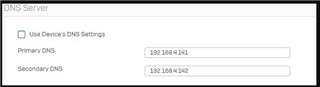
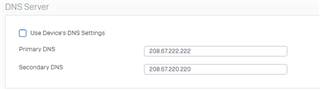
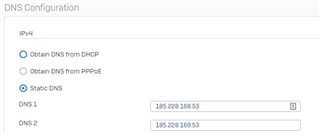
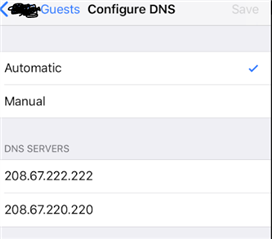
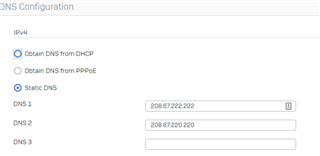
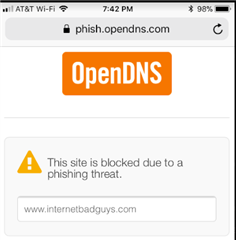
I'm noticing that regardless of the DNS server the client is set to use, the DNS servers set in the DNS tab of the network settings are the one that ends up being used (XG intercepting the DNS Traffic?). To test this, I set a client to specifically use OpenDNS via DHCP settings, verified the setting was applied via ipconfig /all, and tested against a known FQDN OpenDNS blocks. To my surprise, I received the blocked page of the other DNS content filtering provider that was specified in the DNS tab of the XG. If I change the server in that tab to OpenDNS, I do receive the OpenDNS blocked page. Changing whether "DNS" is enabled in the zone configuration page does not seem to make a difference.
I need a way specify DNS servers for each network zone so that different DNS filtering policies are applied by the DNS content filter. Is this possible?
Thanks for any ideas/help you can provide!
This thread was automatically locked due to age.