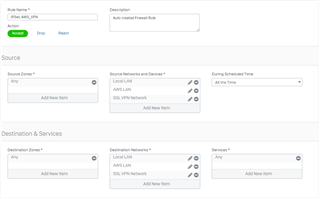
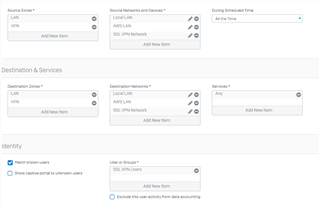
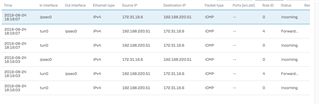
Having an issue with an SSL VPN passing traffic through the main office to AWS that is connected via IPSec VPN
Traffic is passing just fine from the main office to AWS, but when we connect to the XG via SSL VPN we can't get the traffic to pass through to the AWS network.
Firewall Rules
Any suggestions?
This thread was automatically locked due to age.