Topology: Internet<--><50.x.y.228[MikroTik]192.168.z.9><--><192.168.z.129[XG]
- The subnet between the XG and the MikroTik is 192.168.z.0/22.
- Port2 and Port4 are bridged.
- The connection to the MikroTik is on XG Port2.
- The connection to all other computers and devices is on XG Port4
- STAS is not active.
When I Browse from the Internet to 50.x.y.228, my traffic is forwarded to the XG as 192.168.z.57. The firewall rule passes some of the traffic and the server at .57 responds. Some of the traffic is dropped by rule 0. In my browser, I get the XG's dropped ice cream cone "Website not available" message.
Packet capture:
| 9/20/2018 15:48 | Port2 | IPv4 | 50.x.y.110 | 192.168.z.57 | TCP | 50333,80 | 3 | Consumed | No Policy | No Policy |
| 9/20/2018 15:48 | Port2 | IPv4 | 50.x.y.110 | 192.168.z.57 | TCP | 50333,80 | 0 | Incoming | No Policy | No Policy |
| 9/20/2018 15:48 | Port2 | IPv4 | 50.x.y.110 | 192.168.z.57 | TCP | 50333,80 | 3 | Consumed | No Policy | No Policy |
| 9/20/2018 15:48 | Port2 | IPv4 | 50.x.y.110 | 192.168.z.57 | TCP | 50333,80 | 0 | Incoming | No Policy | No Policy |
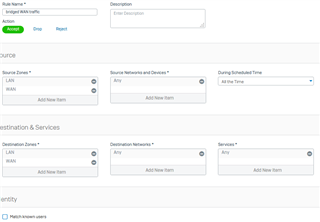
Firewall rule #3:
Why are those packets dropped when I select 'Scan HTTP" in the firewall rule?
Cheers - Bob
This thread was automatically locked due to age.