Dear Sophos XG users.
I am attempting something that can be done on PFSense, but I am having issues replicating the setup on my Sophos XG at home.
Within PFSense, you can setup a VPN Client via IPSec that allows you to forward all WAN traffic over the VPN first, so all data behind the firewall is encrypted as it leaves to go to the internet.
I assumed that it would be possible to also do this using a host to host IPSec VPN configuration within Sophos XG.
Here is my current setup:
- I have a Sophos XG210 with Home installed on it
- I have a VPS Service with PrivateInternetAccess, which supports IPSec
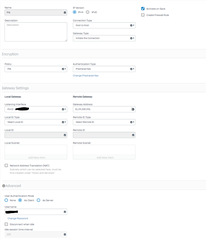
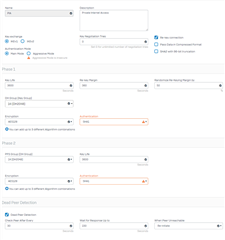
- I have configured a Host2Host configuration and a separate IPSec Policy
- PIA supports 2048 and 4096 DH Modes (using 2048 for now)
Host to Host configuration:
PIA IPSec Policy:
The IPSec Logs seem to throw an AUTH_FAILED error, which investigation seems to be a Phase1 issue, but my usernames / passwords are all correct.
2018-09-23 14:27:22 29[MGR] <PIA-1|2130> Initiating CHILD_SA with configuration PIA-1
2018-09-23 14:27:22 29[IKE] <PIA-1|2130> initiating Main Mode IKE_SA PIA-1[2130] to 31.24.226.241
2018-09-23 14:27:22 29[ENC] <PIA-1|2130> generating ID_PROT request 0 [ SA V V V V V V ]
2018-09-23 14:27:22 29[NET] <PIA-1|2130> sending packet: from xx.xx.xx.xx[500] to 31.24.226.241[500] (260 bytes)
2018-09-23 14:27:22 31[NET] <PIA-1|2130> received packet: from 31.24.226.241[500] to xx.xx.xx.xx[500] (136 bytes)
2018-09-23 14:27:22 31[ENC] <PIA-1|2130> parsed ID_PROT response 0 [ SA V V V ]
2018-09-23 14:27:22 31[IKE] <PIA-1|2130> received XAuth vendor ID
2018-09-23 14:27:22 31[IKE] <PIA-1|2130> received DPD vendor ID
2018-09-23 14:27:22 31[IKE] <PIA-1|2130> received NAT-T (RFC 3947) vendor ID
2018-09-23 14:27:22 31[ENC] <PIA-1|2130> generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
2018-09-23 14:27:22 31[NET] <PIA-1|2130> sending packet: from xx.xx.xx.xx[500] to 31.24.226.241[500] (372 bytes)
2018-09-23 14:27:22 25[NET] <PIA-1|2130> received packet: from 31.24.226.241[500] to xx.xx.xx.xx[500] (372 bytes)
2018-09-23 14:27:22 25[ENC] <PIA-1|2130> parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
2018-09-23 14:27:22 25[ENC] <PIA-1|2130> generating ID_PROT request 0 [ ID HASH ]
2018-09-23 14:27:22 25[NET] <PIA-1|2130> sending packet: from xx.xx.xx.xx[500] to 31.24.226.241[500] (76 bytes)
2018-09-23 14:27:22 21[NET] <PIA-1|2130> received packet: from 31.24.226.241[500] to xx.xx.xx.xx[500] (92 bytes)
2018-09-23 14:27:22 21[ENC] <PIA-1|2130> parsed INFORMATIONAL_V1 request 1372697593 [ HASH N(AUTH_FAILED) ]
2018-09-23 14:27:22 21[IKE] <PIA-1|2130> received AUTHENTICATION_FAILED error notify
2018-09-23 14:27:22 21[IKE] <PIA-1|2130> IKE_SA AUTHENTICATION_FAILED set_condition COND_START_OVER
2018-09-23 14:27:22 21[IKE] <PIA-1|2130> IKE_SA has_condition COND_START_OVER retry initiate in 60 sec
Has anyone else attempted something like this, and got it working - or should i shove a PFSense box between sophos and my WAN (even if that makes my networking OCD trigger)
This thread was automatically locked due to age.