Hey all,
I want to block all internet access to a machine. The machine can only access the web if it passes via a VPN client (PIA in my case)
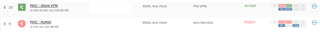
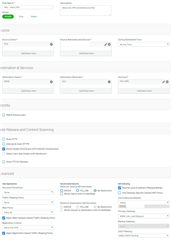
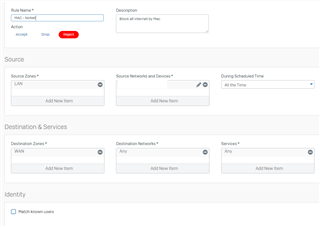
Currently I have made this setup:
with service
and
By the looks of it it works.
Am I missing something? Is there a better way?
Thanks,
This thread was automatically locked due to age.