Hi,
I managed to get two WLAN networks working on the Sophos XG using our existing Unify AP's.
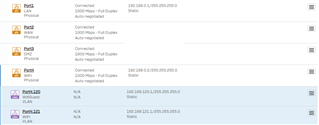
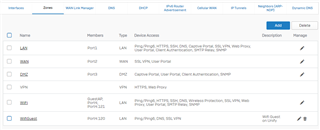
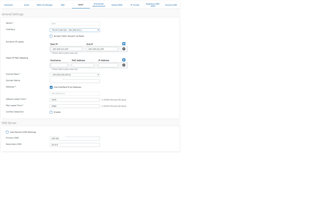
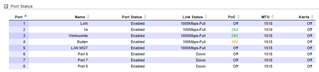
Port4, zone wifi, static gateway address in the LAN range, LAN Relay
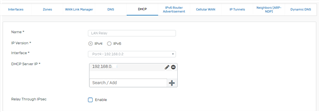
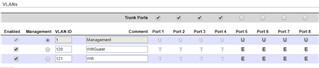
Port4.120 WifiGuest, DHCP server with IP address 192.168.120.x
Port4.121 Wifi, DHCP server IP address 192.168.121.x
Firewall rules allow the WifiGuest network access to a guest printer in the LAN, and the WAN. The Wifi has full access to the local LAN.
Sofar so good. However, For some reason there is no LAN connection on Port4.
The AP's are connected to an EdgeSwitch, with a trunk on port 1 connecting the Unlabeled Management interface, and the two VLAN's. The switch port 1 is connected to the Port4 of the Sophos.
I can get it to work by connecting a separate port of the EdgeSwitch to the LAN switch, but I would like to understand the configuration better, and I think it should be able to work with the Port4 interface.
Any suggestions?
This thread was automatically locked due to age.