Recently I purchased an XG 105 firewall to place in my dataroom. The device is installed in bridge mode.
When I bypass the device, I reach speeds of 30 MB/sec (on a 1 Gbit/sec connection)
When the traffic is going of the XG 105 in bridge mode, speeds are usually between 5 MB/sec and 8 MB/sec.
The traffic that is being generated at that point in time is VEEAM traffic.
I have checked the switchports, but not a single input nor output error is detected, so that seems to be OK.
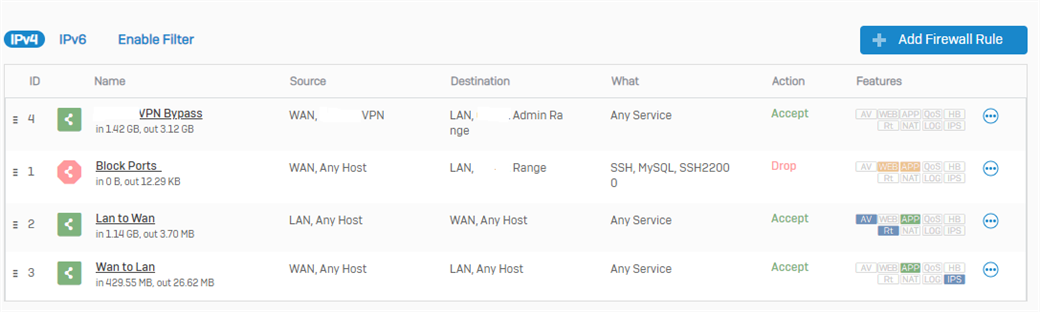
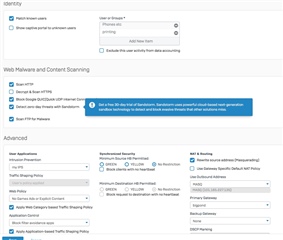
At first I thought it might be due to IPS or application detection, so I created a separate firewall rule that allows the VEEAM traffic and not do any kind of IPS or scanning on this traffic. You can see the amount of GB's increased on this particular firewall rule, so I'm pretty sure the right one is hit.
But despite this rule, still my speeds are much slower compared to when I don't have the Sophos XG 105 in between.
The CPU is around 30% when the traffic is flowing, and memory usage around 80%, normal values I presume.
Is there anybody who could give me some pointers about why traffic is so much slower when passing through the XG firewall?
Thank you!
This thread was automatically locked due to age.