There's a list of entries in my firewall log of traffic being 'Denied' but I'm not sure what's causing it and why it's being blocked.
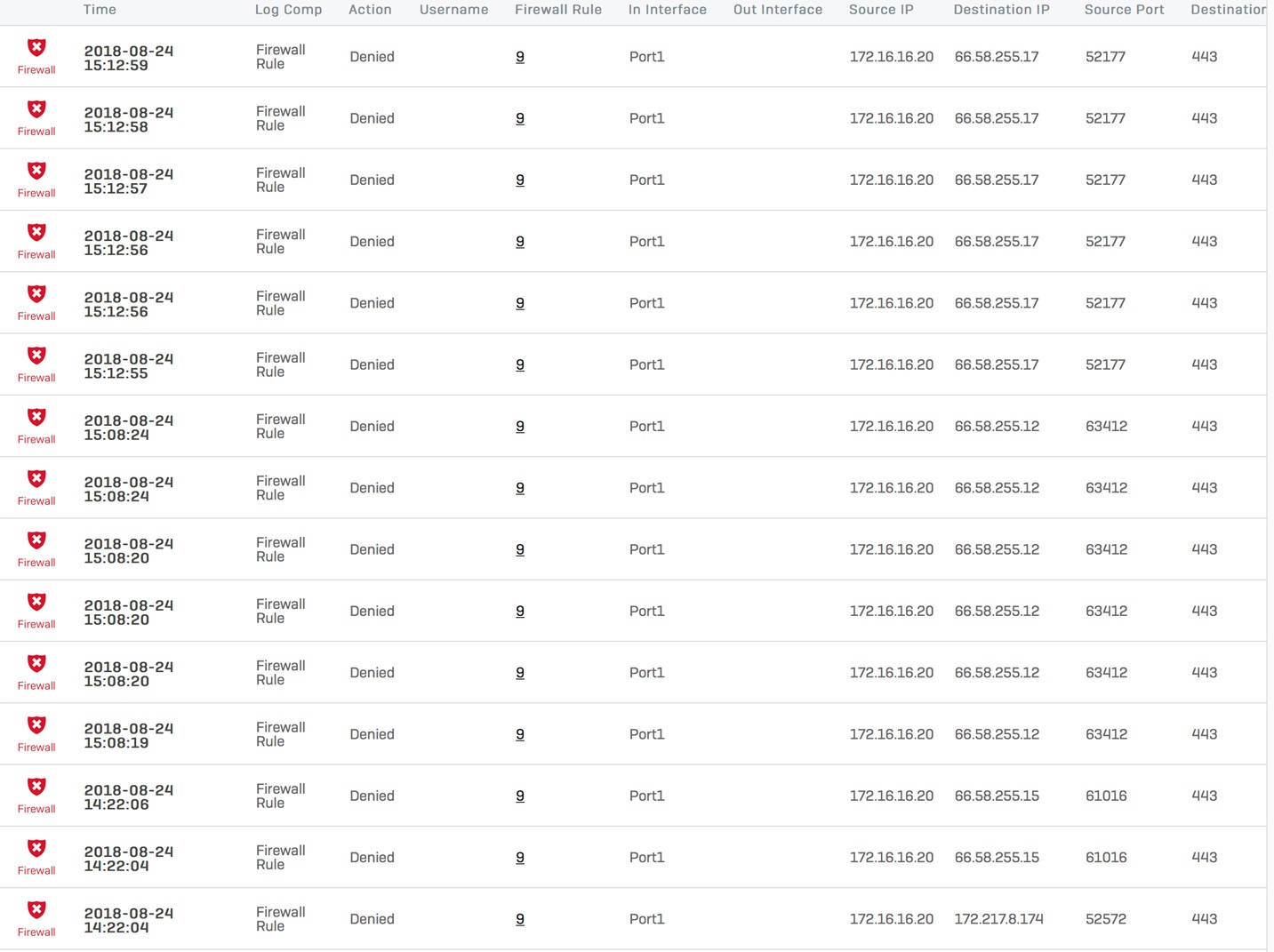
Here's a screenshot of the firewall log:
Here's the detailed description from one of the entries:
2018-08-24 15:12:59Firewallmessageid="00002" log_type="Firewall" log_component="Firewall Rule" log_subtype="Denied" status="Deny" con_duration="0" fw_rule_id="9" policy_type="1" user="" user_group="" web_policy_id="12" ips_policy_id="12" appfilter_policy_id="10" app_name="" app_risk="0" app_technology="" app_category="" in_interface="Port1" out_interface="" src_mac="[removed]" src_ip="172.16.16.20" src_country="" dst_ip="66.58.255.17" dst_country="" protocol="UDP" src_port="52177" dst_port="443" packets_sent="0" packets_received="0" bytes_sent="0" bytes_received="0" src_trans_ip="" src_trans_port="0" dst_trans_ip="" dst_trans_port="0" src_zone_type="" src_zone="" dst_zone_type="" dst_zone="" con_direction="" con_id="" virt_con_id="" hb_status="No Heartbeat" message="" appresolvedby="Signature" app_is_cloud="0"
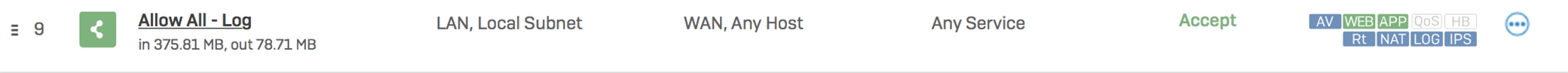
Here's a screenshot of firewall rule 9:
The destination IP addresses appear to be Google's main page. My only guess is because there's no 'Out Interface' defined, so the traffic is being blocked because it's not matching any Zones I have defined in my firewall rules.
Any ideas?
This thread was automatically locked due to age.